111 million ZK tokens were suddenly stolen. Is the story of ZKsync going to an end?

Reprinted from panewslab
04/16/2025·4DRecently, the industry has collective Mercury retrograde and security incidents have occurred frequently.
On the evening of April 15, ZKsync, who was once one of the "Four Heavenly Kings" of L2, was exposed for a project token security incident, but the information was not disclosed first by the project party. Last night, community members disclosed that Zksync issued 110 million tokens on the chain and has continuously sold 66 million tokens on the chain, but according to the token unlock information, the team and investor tokens are still locked.
Affected by this news, ZK fell below 0.04 USDT within half an hour, hitting a minimum of 0.03972 USDT. South Korean exchange Bithumb said it found that ZK had security problems and temporarily suspended ZK charging and withdrawal business until the market was ensured to be stable. ZKsync's official also responded on the official Discord that an investigation is being carried out.
Just when the community speculated that this incident was the project party's initiative to issue additional tokens to do evil, ZKsync issued an announcement stating:
After investigation, the security incident was hacked due to the leakage of the administrator account key of the three airdrop distribution contracts. The attacker called the sweepUnclaimed() function and minted about 111 million non-approved ZK tokens from the aidrop contract, increasing the supply of tokens in circulation by about 0.45%, worth about 5 million US dollars. However, the attack only involves the ZK token airdrop allocation contract, and the ZKsync protocol, the ZK token contract, all three governance contracts, and all active token plan cap minters were not affected by the incident. Recovery work is currently being coordinated with the exchange, and the attacker is advised to return funds and avoid legal liability.
The investigation is still underway and detailed updates will be released later.
The actual stolen token was 2 days ago
However, such an official explanation cannot convince the community -according to on-chain data, the hacker had already minted 111 million tokens from the ZK token airdrop allocation contract at 20:00 on April 13 (UTC+8), and immediately began to transfer and sell cross-chain continuously. So far, there are only about 44.68 million ZKs left in the account, worth about 2.12 million US dollars, still accounting for 0.34% of the token supply.
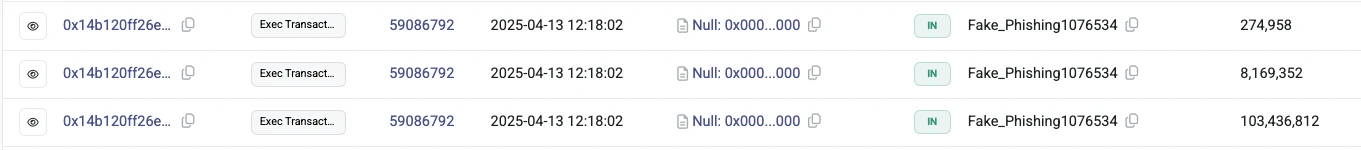
Hacker successfully attacked on April 13
Therefore, it can also be concluded that the decline in the price of ZK tokens last night was not entirely caused by hacker sell-offs, but was mainly due to the leak of the theft scandal, which caused panic selling in the community.
Although the price of ZK tokens has now rebounded to above 0.045USDT, it is worth thinking that the airdrop token has actually been stolen, but it was only disclosed by the community for the first time two days later. Was ZKsync really unaware of it or was it deliberately concealed to avoid community riots? If ZKsync really only learned about the information and launched an investigation through community channels, then he couldn't help but sigh that behind this former king-level project was a group of "grass teams", and he was still unaware of it.
The community reasonably speculated that this incident was a custody of internal members. Could it be that the airdrop contract administrator account key was kept by one person? At the same time, since the incident has occurred, how should the subsequent stolen funds be handled? Can it be successfully frozen or repurchased? These questions are subject to answer by the team. The final investigation results will also continue to follow up the reports.
What kind of ending has ZKsync headed?
This incident also highlights the risks brought by centralized administrator rights in the originally decentralized system. Strong account access control is as important as smart contract security itself, and the security of administrator keys can also seriously affect the security of encryption projects and should not be discussed separately.
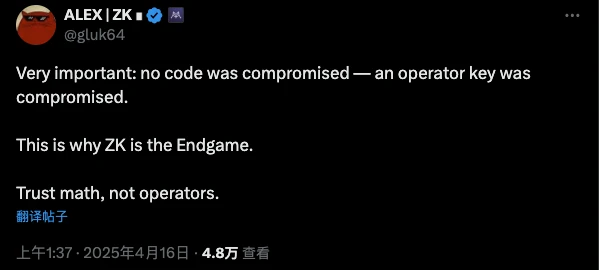
However, just when the hackers were still selling coins happily, the founder of ZKsync also said confidently on the X platform, "In this attack, the project code was not leaked, it was just the administrator key leak, which is why ZK is the end."
Technologies such as ZK verification have always been claimed to have better security than Optimistic Proof (Op), and were once considered the final technical form of Ethereum L2, namely Endgame. However, although the token theft incident did not involve core project tokens, the protection measures for airdrop allocation contracts were too weak, as if the walls of an advanced high-tech building were filled with straw for building houses in ancient times.
When facing the community’s questioning “Since as one of the leaders in the ZK field, why didn’t we foresee this attack”, the founder of ZKsync was able to respond shamelessly that “the black swan could not be foreseeable.” The stolen permission account key is the most common way of attack for blockchain projects. Just like the phishing users face every day, ZKsync does not strengthen security protection measures in advance and defines everything as a black swan, which also reflects the team's weak security awareness.
In addition, how does ZKsync perform in practical applications? According to DeFiLlama data, ZKsync currently has a TVL of US$55.29 million, ranking 52nd, while its 24-hour chain revenue is only US$2,178, and its daily revenue has been below US$5,000 since September 2024. By comparison, Arbitrum still earns more than $10,000 per day. ZKsync has become a veritable "ghost chain".
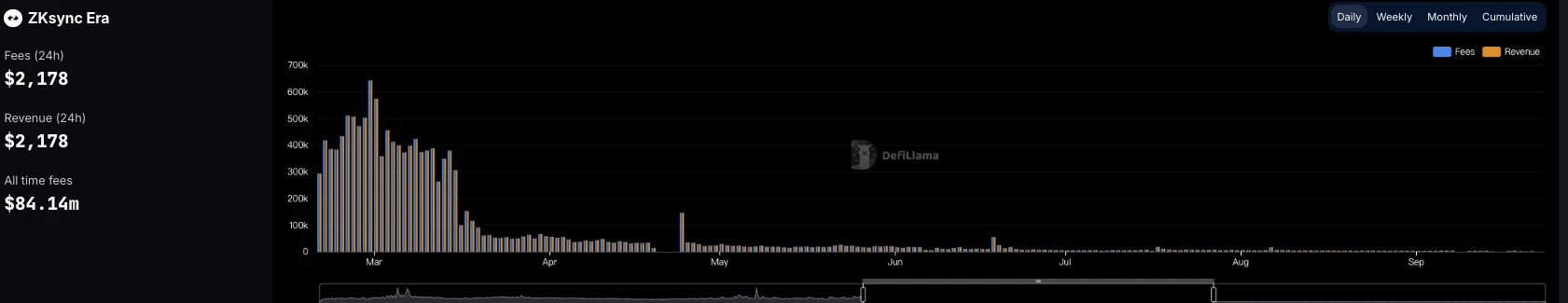
ZKsync is heading towards Endgame. This is not the perfect ending after the superhero defeated the boss in the movie, but the black screen ending in the game that was killed because of Taicai. But before being completely killed, I hope ZKsync can save the trapped investors first.

 chaincatcher
chaincatcher