In-depth investigation into the Rug Pull case to reveal the ecological chaos of Ethereum tokens

Reprinted from panewslab
01/08/2025·1MIntroduction
In the Web3 world, new tokens are constantly emerging. Have you ever wondered how many new tokens are issued every day? Are these new coins safe?
These questions are not without purpose. Over the past few months, the CertiK security team has captured a large number of Rug Pull transactions. It is worth noting that the tokens involved in these cases are all new tokens that have just been put on the chain.
Subsequently, CertiK conducted in-depth investigations into these Rug Pull cases and found that there were organized criminal gangs behind them, and summarized the pattern characteristics of these scams. Through in-depth analysis of the modus operandi of these gangs, CertiK discovered a possible fraud promotion method of the Rug Pull gang: Telegram groups. These gangs use the "New Token Tracer" function in groups such as Banana Gun and Unibot to attract users to purchase fraudulent tokens and ultimately make profits through Rug Pull.
CertiK counted the token push information of these Telegram groups from November 2023 to early August 2024, and found that a total of 93,930 new tokens were pushed, of which 46,526 tokens involved Rug Pull, accounting for 49.53% . According to statistics, the cumulative investment cost of the group behind these Rug Pull tokens was 149,813.72 ETH, and they made a profit of 282,699.96 ETH at a rate of return of up to 188.7%, equivalent to approximately US$800 million.
In order to evaluate the proportion of new tokens pushed by Telegram groups in the Ethereum main network, CertiK collected data on new tokens issued on the Ethereum main network during the same time period. Data shows that a total of 100,260 new tokens were issued during this period, of which tokens pushed through Telegram groups accounted for 89.99% of the main network. On average, about 370 new tokens are created every day, far exceeding reasonable expectations. After continued in-depth investigation, we discovered the disturbing truth - at least 48,265 tokens were involved in Rug Pull scams, accounting for a whopping 48.14%. In other words, almost one out of every two new tokens on the Ethereum mainnet is involved in a scam.
In addition, CertiK discovered more Rug Pull cases in other blockchain networks. This means that not only the Ethereum mainnet, but also the security situation of the entire Web3 newly issued token ecosystem is far more severe than expected. Therefore, CertiK wrote this research report, hoping to help all Web3 members increase their awareness of prevention, stay vigilant in the face of endless scams, and take necessary preventive measures in a timely manner to protect the security of their assets.
ERC-20 Token
Before we officially start this report, let's first understand some basic concepts.
ERC-20 tokens are currently one of the most common token standards on the blockchain. They define a set of specifications that allow tokens to interoperate between different smart contracts and decentralized applications (dApps). . The ERC-20 standard stipulates the basic functions of tokens, such as transferring funds, checking balances, authorizing third parties to manage tokens, etc. Thanks to this standardized protocol, developers can issue and manage tokens more easily, simplifying token creation and usage. In fact, any individual or organization can issue their own tokens based on the ERC-20 standard and raise startup funds for various financial projects through pre-sale of tokens. Because of the wide application of ERC-20 tokens, it has become the basis for many ICO and decentralized finance projects.
The familiar USDT, PEPE, and DOGE are all ERC-20 tokens, and users can purchase these tokens through decentralized exchanges. However, some fraud groups may also self-issue malicious ERC-20 tokens with code backdoors, list them on decentralized exchanges, and then induce users to purchase them.
Typical scam cases of Rug Pull tokens
Here, we use a Rug Pull token fraud case to gain an in-depth understanding of the operating model of malicious token fraud. First of all, it needs to be explained that Rug Pull refers to a fraudulent behavior in which the project party suddenly withdraws funds or abandons the project in a decentralized financial project, causing investors to suffer huge losses. The Rug Pull token is a token specifically issued to carry out this kind of fraud.
The Rug Pull tokens mentioned in this article are sometimes also called "Honey Pot tokens" or "Exit Scam tokens", but in the following we will refer to them as Rug Pull tokens. .
· Case
The attacker (Rug Pull gang) deployed TOMMI tokens with the Deployer address (0x4bAF), then created a liquidity pool with 1.5 ETH and 100,000,000 TOMMI, and actively purchased TOMMI tokens through other addresses to fake the liquidity pool transaction volume to attract Users and new robots on the chain purchase TOMMI tokens. When a certain number of new robots were fooled, the attacker used the Rug Puller address (0x43a9) to execute the Rug Pull. The Rug Puller used 38,739,354 TOMMI tokens to pour into the liquidity pool and redeemed approximately 3.95 ETH. Rug Puller's tokens come from the malicious Approve authorization of the TOMMI token contract. When the TOMMI token contract is deployed, it will grant Rug Puller the approve permission of the liquidity pool, which allows Rug Puller to directly transfer TOMMI tokens from the liquidity pool. Then do the Rug Pull.
·Related addresses
- Deployer: 0x4bAFd8c32D9a8585af0bb6872482a76150F528b7
- TOMMI Token: 0xe52bDD1fc98cD6c0cd544c0187129c20D4545C7F
- Rug Puller: 0x43A905f4BF396269e5C559a01C691dF5CbD25a2b
- Rug Puller disguised user (one of them): 0x4027F4daBFBB616A8dCb19bb225B3cF17879c9A8
- Rug Pull fund transfer address: 0x1d3970677aa2324E4822b293e500220958d493d0
- Rug Pull fund retention address: 0x28367D2656434b928a6799E0B091045e2ee84722
·Related transactions
- Deployer obtains startup funds from centralized exchanges: 0x428262fb31b1378ea872a59528d3277a292efe7528d9ffa2bd926f8bd4129457
- Deploy TOMMI token: 0xf0389c0fa44f74bca24bc9d53710b21f1c4c8c5fba5b2ebf5a8adfa9b2d851f8
- Create a liquidity pool: 0x59bb8b69ca3fe2b3bb52825c7a96bf5f92c4dc2a8b9af3a2f1dddda0a79ee78c
- The fund transfer address sends funds to the disguised user (one of them): 0x972942e97e4952382d4604227ce7b849b9360ba5213f2de6edabb35ebbd20eff
- Pretend user to purchase tokens (one of them): 0x814247c4f4362dc15e75c0167efaec8e3a5001ddbda6bc4ace6bd7c451a0b231
- Rug Pull: 0xfc2a8e4f192397471ae0eae826dac580d03bcdfcb929c7423e174d1919e1ba9c
- Rug Pull will send the funds obtained to the transfer address: 0xf1e789f32b19089ccf3d0b9f7f4779eb00e724bb779d691f19a4a19d6fd15523
- The transfer address sends funds to the fund retention address: 0xb78cba313021ab060bd1c8b024198a2e5e1abc458ef9070c0d11688506b7e8d7
· Rug Pull process
1. Prepare attack funds.
The attacker recharged 2.47309009 ETH to Token Deployer (0x4bAF) through the centralized exchange as the starting capital for Rug Pull.
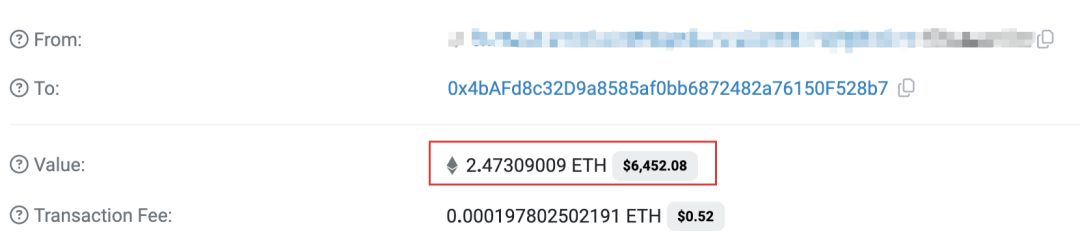
Figure 1 Deployer obtains startup capital transaction information from the exchange
2. Deploy the Rug Pull token with backdoor.
Deployer creates TOMMI tokens, premines 100,000,000 tokens and allocates them to itself.
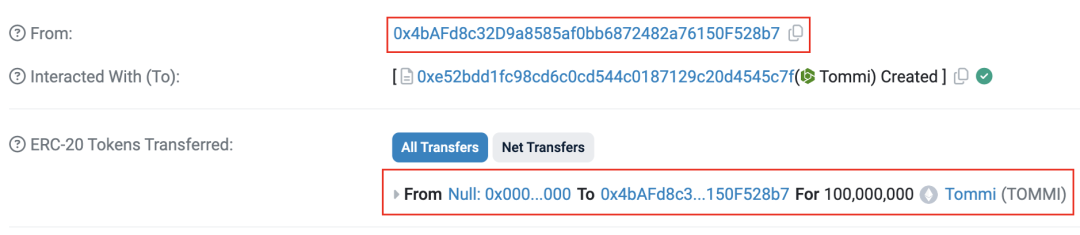
Figure 2 Deployer creates TOMMI token transaction information
3. Create an initial liquidity pool.
Deployer used 1.5 ETH and all pre-mined tokens to create a liquidity pool and obtained approximately 0.387 LP tokens.
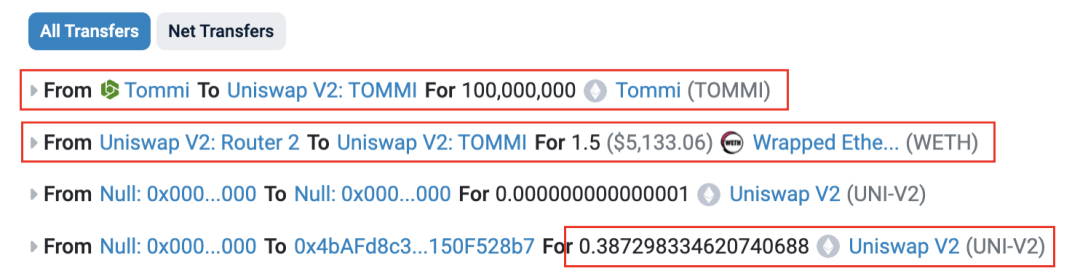
Figure 3 Deployer creates a liquidity pool and trades fund flows
4. Destroy all pre-mined Token supply.
Token Deployer sends all LP tokens to the 0 address for destruction. Since there is no Mint function in the TOMMI contract, Token Deployer has theoretically lost its Rug Pull capability at this time. (This is also one of the necessary conditions to attract new robots to enter the market. Some new robots will evaluate whether newly added tokens to the pool are at risk of rug pull. Deployer will also set the owner of the contract to the 0 address, all in order to deceive new robots. Robot anti-fraud program).
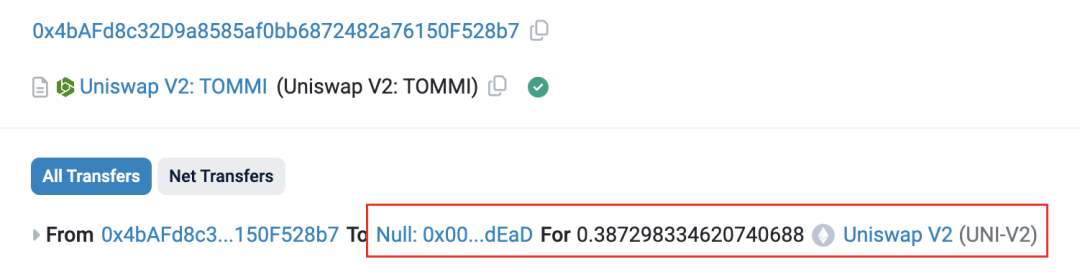
Figure 4 Deployer destroys LP token transaction information
5. Falsifying trading volume.
The attacker uses multiple addresses to actively purchase TOMMI tokens from the liquidity pool, increasing the transaction volume of the pool, and further attracting new robots to enter the market (the basis for judging that these addresses are the attacker's disguise: the funds for the relevant addresses come from the Rug Pull gang) historical fund transfer address).
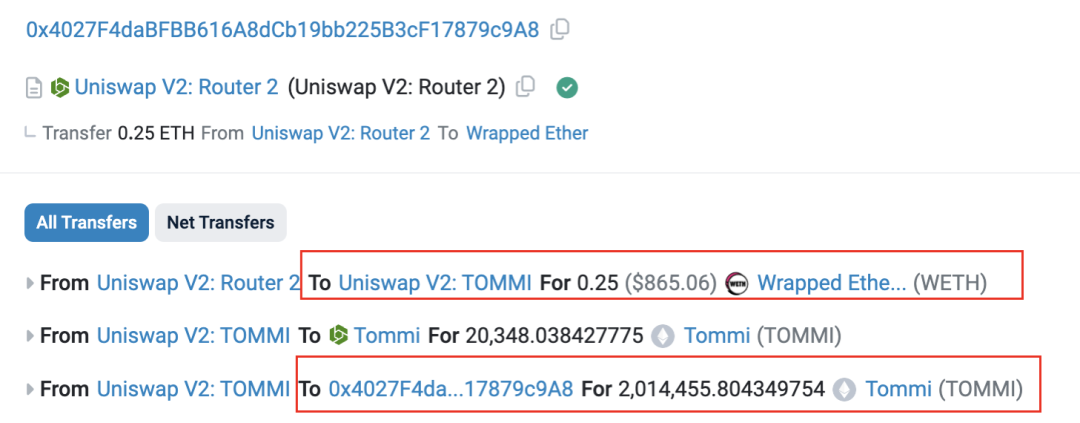
Figure 5 Transaction information and fund flows of attackers purchasing TOMMI tokens from other addresses
6. The attacker initiated a Rug Pull through the Rug Puller address (0x43A9), transferred 38,739,354 tokens directly from the liquidity pool through the token’s backdoor, and then used these tokens to sink the pool, extracting approximately 3.95 ETH.
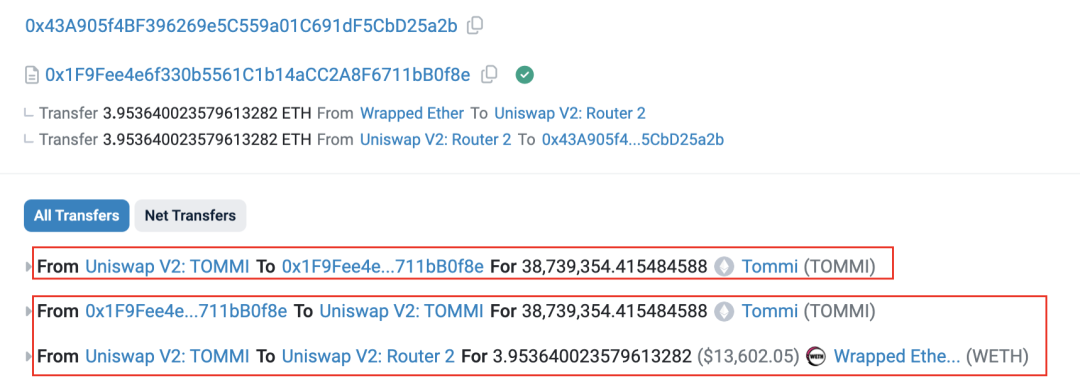
Figure 6 Rug Pull transaction information and capital flow
7. The attacker sends the funds obtained from the Rug Pull to the transit address 0xD921.
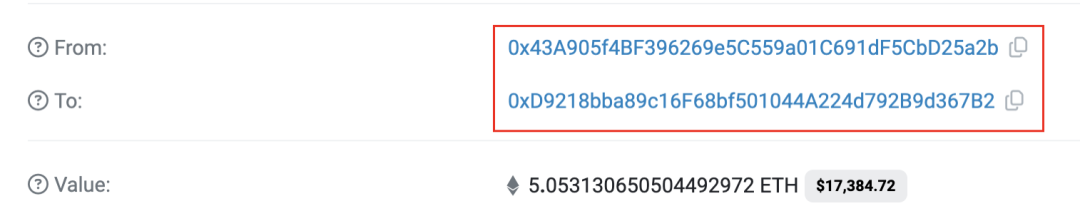
Figure 7 Rug Puller sends attack proceeds to the transit address transaction information
8. The transfer address 0xD921 sends the funds to the fund retention address 0x2836. From here we can see that when the Rug Pull is completed, the Rug Puller will send the funds to a certain fund retention address. The fund retention address is where the funds for a large number of Rug Pull cases that we monitor are gathered. The fund retention address will split most of the funds received to start a new round of Rug Pull, while the remaining small amount of funds will go through centralized transactions. Withdrawal. We found several fund retention addresses, and 0x2836 is one of them.
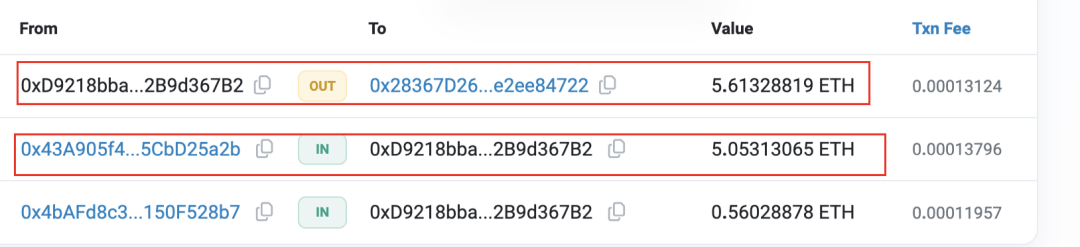
Figure 8 Transfer address fund transfer information
· Rug Pull code backdoor
Although the attacker has tried to prove to the outside world that they cannot perform Rug Pull by destroying LP tokens, in fact the attacker has left a malicious approve backdoor in the openTrading function of the TOMMI token contract. This backdoor will create a flow When using the liquidity pool, let the liquidity pool approve the transfer permission of tokens to the Rug Puller address, so that the Rug Puller address can directly transfer tokens from the liquidity pool.
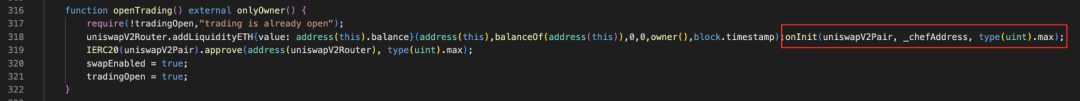
Figure 9 openTrading function in TOMMI token contract
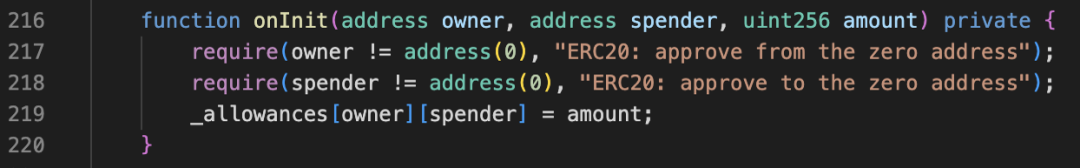
Figure 10 onInit function in TOMMI token contract
The implementation of the openTrading function is shown in Figure 9. Its main function is to create a new liquidity pool, but the attacker called the backdoor function onInit within this function (shown in Figure 10), allowing uniswapV2Pair to approve the number of _chefAddress addresses. Token transfer permission of type(uint256). Among them, uniswapV2Pair is the liquidity pool address, _chefAddress is the Rug Puller address, and _chefAddress is specified when the contract is deployed (shown in Figure 11).
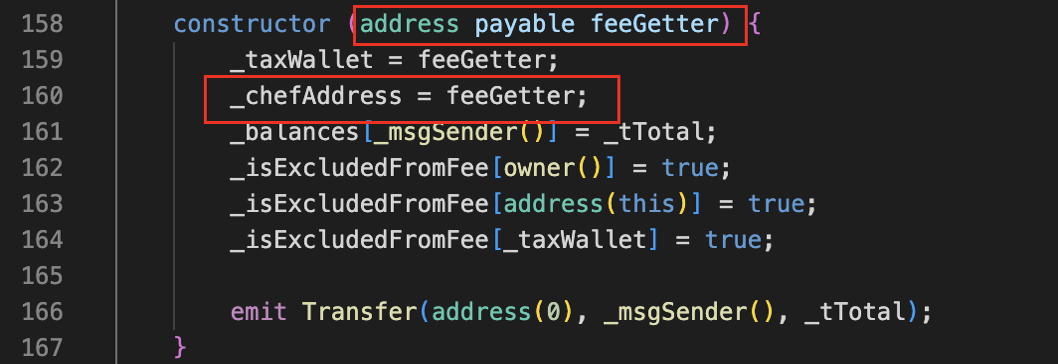
Figure 11 Constructor in TOMMI token contract
·Modeling of crime
By analyzing the TOMMI case, we can summarize the following four characteristics:
1. Deployer obtains funds through a centralized exchange: The attacker first provides a source of funds for the deployer address (Deployer) through a centralized exchange.
2. Deployer creates a liquidity pool and destroys LP tokens: After the deployer creates the Rug Pull token, it will immediately create a liquidity pool for it and destroy the LP token to increase the credibility of the project and attract more investor.
3. Rug Puller uses a large amount of tokens to exchange for ETH in the liquidity pool: The Rug Pull address (Rug Puller) uses a large amount of tokens (usually far exceeding the total supply of tokens) to exchange for ETH in the liquidity pool. In other cases, Rug Puller has also removed liquidity to obtain ETH in the pool.
4. Rug Puller transfers the ETH obtained from Rug Pull to the fund retention address: Rug Puller will transfer the ETH obtained to the fund retention address, sometimes through an intermediate address.
The above characteristics are commonly found in the cases we captured, which shows that Rug Pull behavior has obvious pattern characteristics. In addition, after the Rug Pull is completed, the funds are usually funneled to a fund retention address, which implies that the same group or even the same fraud gang may be involved behind these seemingly independent Rug Pull cases.
Based on these characteristics, we extracted a Rug Pull behavior pattern and used this pattern to scan and detect the monitored cases in order to build a portrait of a possible fraud gang.
Rug Pull gang
· Mining the fund storage address
As mentioned above, Rug Pull cases usually funnel funds to the fund retention address at the end. Based on this model, we selected several highly active fund retention addresses with obvious modus operandi of related cases for in-depth analysis.
A total of 7 fund retention addresses came into our view. There were a total of 1,124 Rug Pull cases associated with these addresses, which were successfully captured by our on-chain attack monitoring system (CertiK Alert). After the Rug Pull gang successfully implements the scam, it will funnel the illegal profits to these fund retention addresses. These fund retention addresses will split the precipitated funds and use them for activities such as creating new tokens and manipulating liquidity pools in new Rug Pull scams in the future. In addition, a small part of the accumulated funds are cashed out through centralized exchanges or flash exchange platforms.
The fund data statistics about the fund retention address are shown in Table 1:
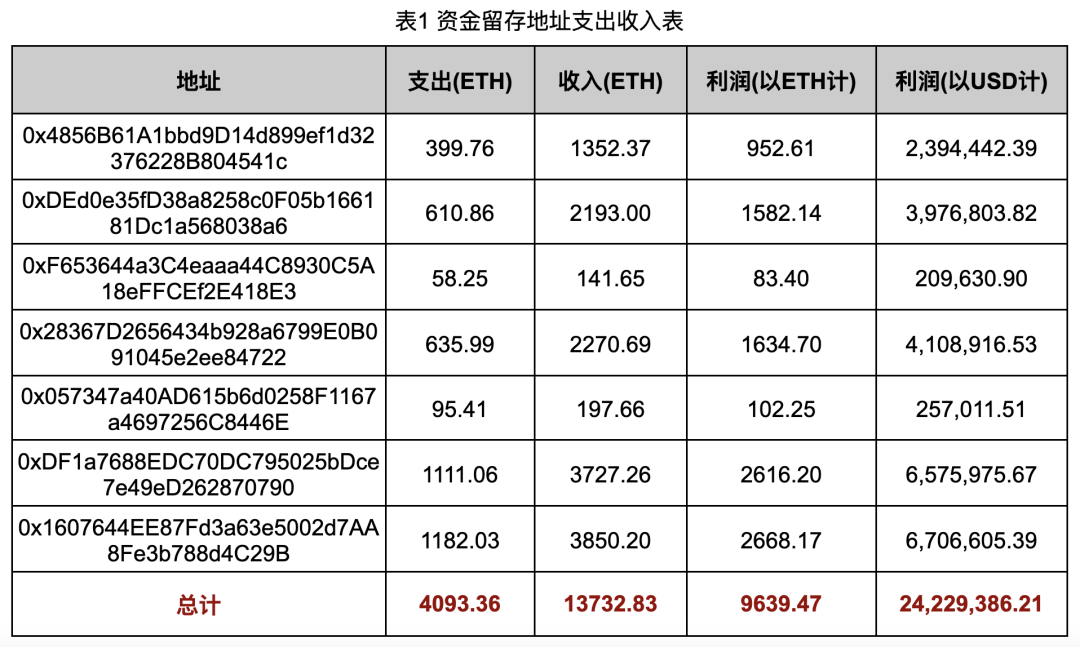
By counting the costs and revenues of all Rug Pull scams in each fund retention address, we obtained the data in Table 1.
In a complete Rug Pull scam, the Rug Pull gang usually uses an address as the deployer of Rug Pull tokens and obtains startup funds through withdrawals from centralized exchanges to create Rug Pull tokens and corresponding liquidity. pool. When a sufficient number of users or new robots are attracted to use ETH to purchase Rug Pull tokens, the Rug Pull gang will use another address as the Rug Pull executor (Rug Puller) to operate and transfer the funds obtained to the fund retention address.
In the above process, we regard the ETH obtained by the Deployer through the exchange, or the ETH invested by the Deployer when creating a liquidity pool, as the cost of Rug Pull (how to calculate it depends on the behavior of the Deployer). The ETH that the Rug Puller transfers to the fund retention address (or other transfer address) after completing the Rug Pull is regarded as the income of the Rug Pull. Finally, the data on income and expenses in Table 1 are obtained, in which the USD Profit Conversion Center The ETH/USD price used (1 ETH = 2,513.56 USD, price acquisition time is August 31, 2024) is calculated based on the real-time price at the time of data integration.
It should be noted that when implementing the scam, the Rug Pull gang will also actively use ETH to purchase the Rug Pull tokens they created to simulate normal liquidity pool activities, thereby attracting new robots to purchase. However, this part of the cost is not included in the calculation, so the data in Table 1 overestimates the actual profits of the Rug Pull gang, and the real profits will be relatively low.
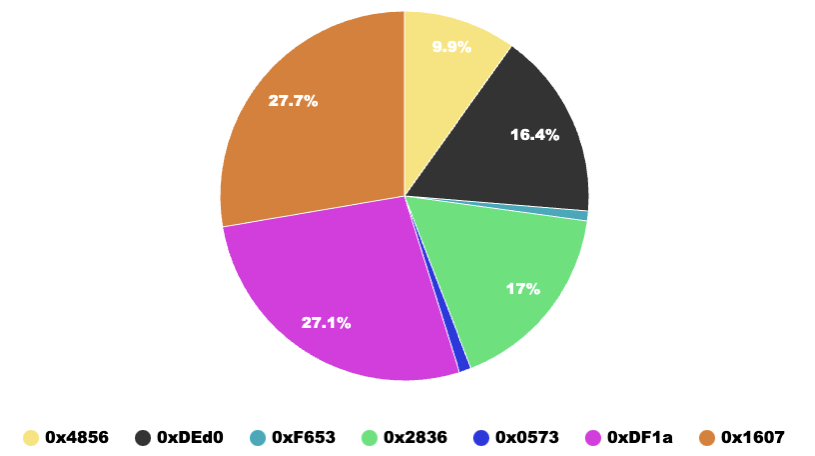
Figure 12 Pie chart of profit ratio of fund retention addresses
Use the Rug Pull profit data of each address in Table 1 to generate a profit proportion pie chart, as shown in Figure 12. The top three addresses with the highest profit share are 0x1607, 0xDF1a and 0x2836. Address 0x1607 earned the highest profit, approximately 2,668.17 ETH, accounting for 27.7% of all address profits.
In fact, even if the funds are ultimately funneled to different fund retention addresses, we are still highly suspicious of these fund retention addresses due to the large number of commonalities between the cases associated with these addresses (such as the backdoor implementation of Rug Pull, cash out paths, etc.) It may be the same gang behind it.
So, is there possibly some connection between these fund retention addresses?
· Mining the correlation between fund retention addresses
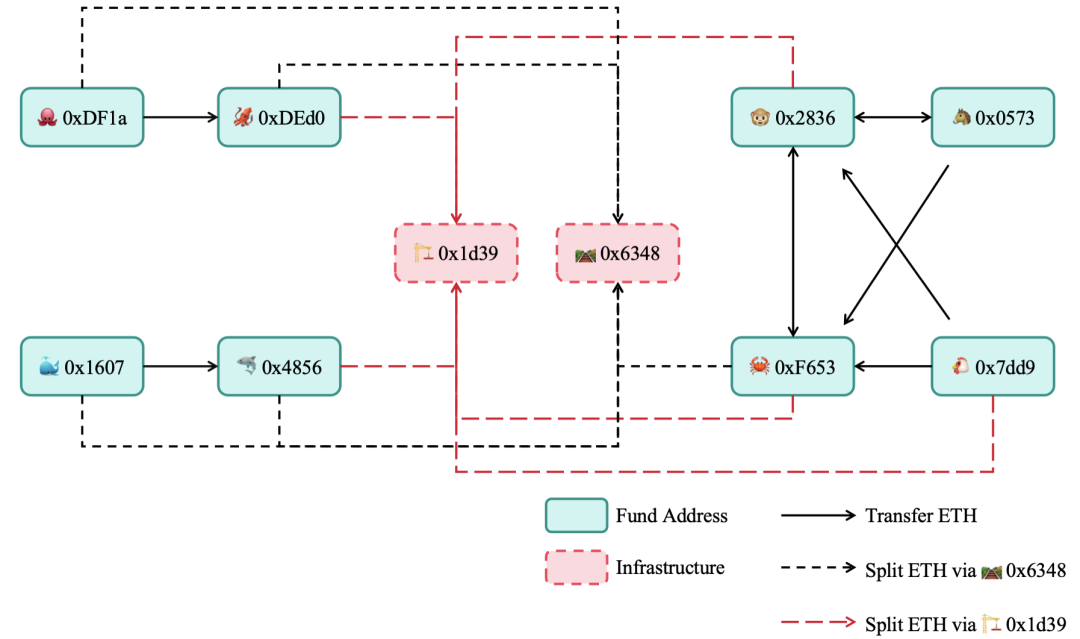
Figure 13 Fund flow diagram of fund retention address
An important indicator to determine whether there is a correlation between fund retention addresses is to see whether there is a direct transfer relationship between these addresses. In order to verify the correlation between the fund retention addresses, we crawled and analyzed the historical transaction records of these addresses.
In most of the cases we have analyzed in the past, the proceeds of each Rug Pull scam will only flow to a certain fund retention address. It is impossible to track the direction of proceeds and associate different fund retention addresses. Therefore, we need to detect the flow of funds between these fund retention addresses in order to obtain the direct correlation between the fund retention addresses. The detection results are shown in Figure 13.
It should be noted that the addresses 0x1d39 and 0x6348 in Figure 13 are the Rug Pull infrastructure contract addresses shared by each fund retention address. The fund retention address splits the funds through these two contracts and sends them to other addresses, and these addresses that receive the split funds use these funds to fake the trading volume of Rug Pull tokens.
According to the direct transfer relationship of ETH in Figure 13, we can divide these fund retention addresses into three address sets:
1. 0xDF1a and 0xDEd0;
2. 0x1607 and 0x4856;
3. 0x2836, 0x0573, 0xF653 and 0x7dd9.
There is a direct transfer relationship within the address collection, but there is no direct transfer behavior between the collections. Therefore, it seems that these 7 fund retention addresses can be divided into 3 different groups. However, these three address sets all split ETH through the same infrastructure contract for subsequent Rug Pull operations, which made the originally seemingly loose three address sets linked together to form a whole. So, does this suggest that the same group is behind these addresses?
This issue will not be discussed in depth here, and everyone can think about the possibilities by themselves.
· Uncovering shared infrastructure
There are two main infrastructure addresses shared by the fund retention addresses mentioned earlier, namely
0x1d3970677aa2324E4822b293e500220958d493d0 and 0x634847D6b650B9f442b3B582971f859E6e65eB53.
Among them, the infrastructure address 0x1d39 mainly contains two functional functions: "multiSendETH" and "0x7a860e7e". The main function of "multiSendETH" is to perform split transfers. The fund retention address splits part of the funds to multiple addresses through the "Multi Send ETH" function of 0x1d39, which is used to forge the transaction volume of Rug Pull tokens. The transaction information is shown in Figure 14 shown.
This split operation helps attackers fake the activity of tokens, making these tokens look more attractive, thereby inducing more users or new bots to buy. Through this method, the Rug Pull gang can further increase the deception and complexity of the scam.
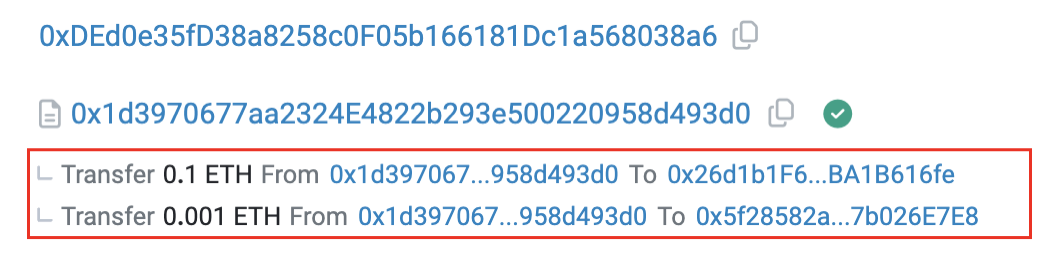
Figure 14 Fund retention address splitting fund transaction information through 0x1d39
The function of "0x7a860e7e" is used to purchase Rug Pull tokens. Other addresses disguised as ordinary users will either directly interact with Uniswap's Router to purchase Rug Pull tokens after receiving the split funds from the fund retention address, or through 0x1d39’s “0x7a860e7e” function purchases Rug Pull tokens to fake active trading volume.
The main functional function of infrastructure address 0x6348 is similar to 0x1d39, except that the function name for purchasing Rug Pull tokens is changed to "0x3f8a436c", which will not be elaborated here.
In order to further understand the use of these infrastructures by the Rug Pull gang, we crawled and analyzed the transaction history of 0x1d39 and 0x6348, and counted the frequency of use of the two functional functions in 0x1d39 and 0x6348 by external addresses. The results are as shown in Table 2 and Table 2 3 shown.
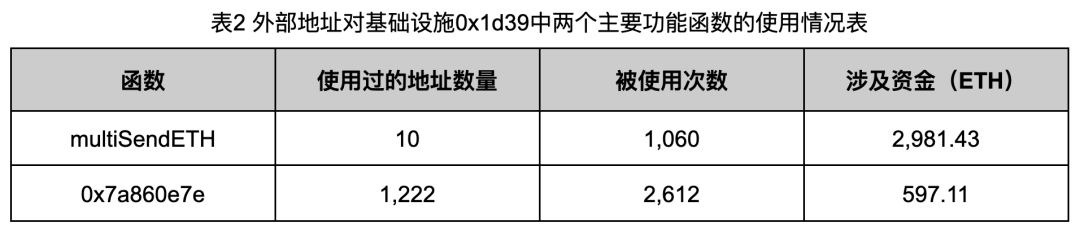
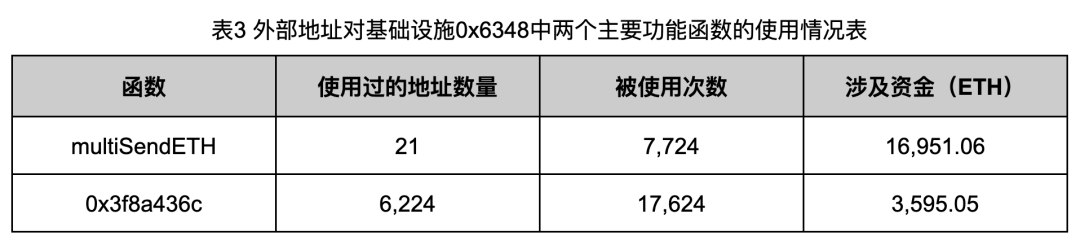
As can be seen from the data in Tables 2 and 3, the Rug Pull gang’s use of infrastructure addresses has obvious characteristics: they only use a small amount of fund retention addresses or transfer addresses to split the funds, but use a large number of other addresses to forge Rug Pull token trading volume. For example, there are even as many as 6,224 addresses that fake transaction volume through address 0x6348. Such a large number of addresses greatly increases the difficulty of distinguishing attacker addresses from victim addresses.
It should be noted that the Rug Pull gang's method of forging transaction volume is not limited to using these infrastructure addresses. Some addresses will also directly exchange tokens through exchanges to forge transaction volume.
In addition, we also counted the usage of each functional function in the two addresses 0x1d39 and 0x6348 by the seven fund retention addresses mentioned above, as well as the amount of ETH involved in each function. The final data are as shown in Table 4 and Table 5 shown.
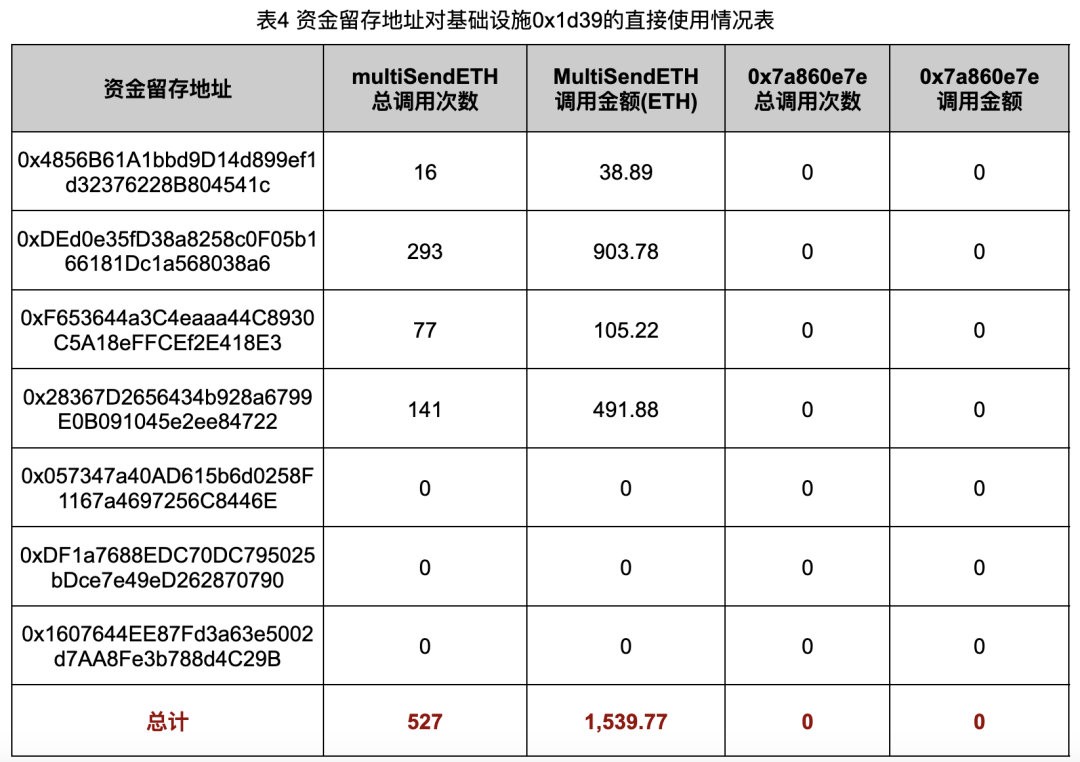
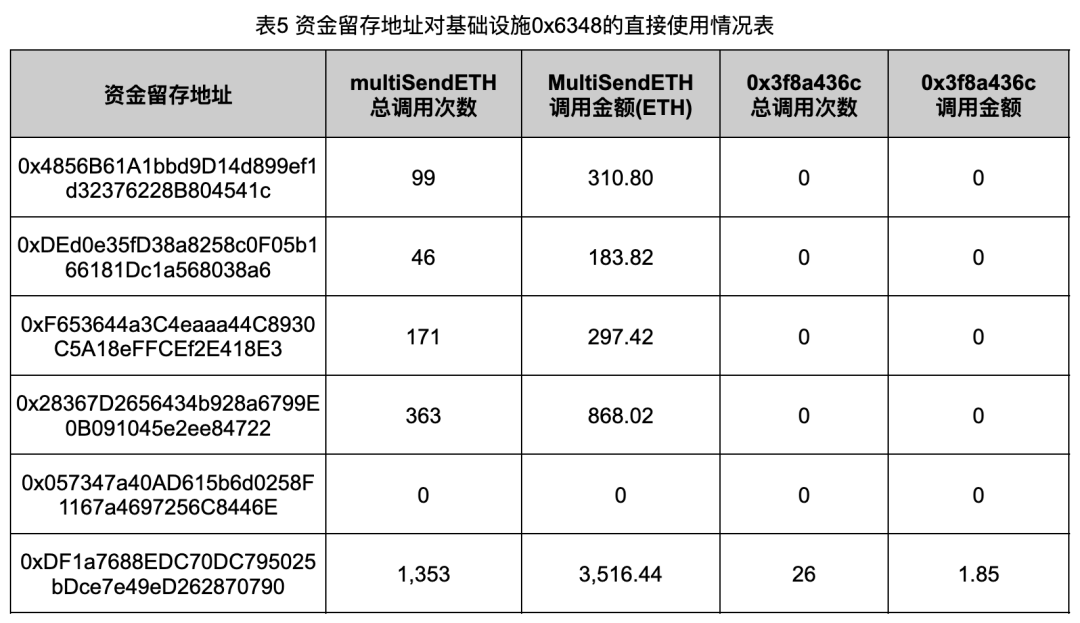
As can be seen from the data in Tables 4 and 5, the fund retention address has split funds a total of 3,616 times through the infrastructure, with the total amount reaching 9,369.98 ETH. Furthermore, with the exception of address 0xDF1a, all fund retention addresses only conduct split transfers through the infrastructure, while purchases of Rug Pull tokens are completed by the addresses that receive these split funds. This shows that these Rug Pull gangs have clear ideas and clear division of labor during their crimes.
Address 0x0573 did not split funds through infrastructure, and the funds used to forge transaction volume in its associated Rug Pull case came from other addresses, which shows that there are certain differences in the crime styles of different fund retention addresses.
By analyzing the financial connections between different fund retention addresses and their use of infrastructure, we have a more comprehensive understanding of the connections between these fund retention addresses. The way these Rug Pull gangs commit crimes is more professional and standardized than we imagined, which further proves that there are criminal groups behind the scenes who carefully plan and operate all of this to carry out systematic fraud activities.
· Digging into the sources of funds for committing crimes
When Rug Pull gangs conduct Rug Pull, they usually use a new external account address (EOA) as a Deployer to deploy Rug Pull tokens, and these Deployer addresses usually obtain startup funds through centralized exchanges or flash swap platforms. To this end, we conducted a fund source analysis on the Rug Pull case associated with the fund retention address mentioned above, aiming to obtain more detailed information on the source of funds for the crime.
Table 6 shows the distribution of the number of Deployer fund source tags associated with Rug Pull cases in each fund retention address.
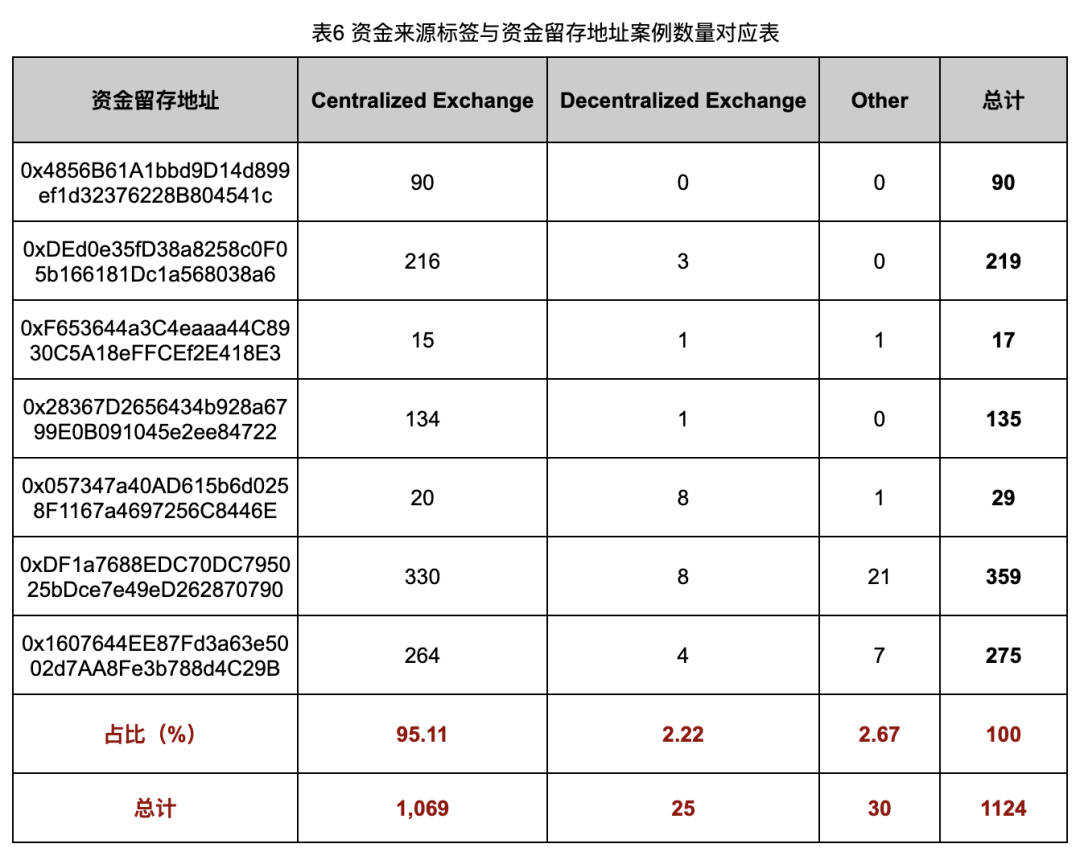
It can be seen from the data in Table 6 that in the Rug Pull cases associated with each fund retention address, most of the Deployer funds for Rug Pull tokens come from centralized exchanges (CEX). Among all the 1,124 Rug Pull cases we analyzed, the number of cases with funds coming from centralized exchange hot wallets reached 1,069, accounting for 95.11%. This means that for the vast majority of Rug Pull cases, we can trace the account KYC information and withdrawal history of the centralized exchange to the specific account holder, thereby obtaining key clues to solve the case.
With in-depth research, we found that these Rug Pull gangs often obtain funds for crimes from multiple exchange hot wallets at the same time, and the usage level (number of uses, proportion) of each wallet is roughly the same. This shows that the Rug Pull gang intends to increase the independence of the capital flow of each Rug Pull case, so as to make it more difficult for outsiders to trace their origins and increase the complexity of tracking.
Through detailed analysis of these fund retention addresses and Rug Pull cases, we can draw a portrait of these Rug Pull gangs: they are well-trained, have a clear division of labor, are premeditated and well-organized. These characteristics demonstrate the high level of professionalism of the gang and the systematic nature of its fraudulent activities.
Faced with such well-organized criminals, we can’t help but have questions and curiosity about their promotion methods: How do these Rug Pull gangs allow users to discover and purchase these Rug Pull tokens? To answer this question, we started focusing on the victim addresses in these Rug Pull cases and tried to reveal how these gangs lured users into participating in their scams.
· Mining victim addresses
Through the analysis of fund correlation, we maintained a list of addresses of the Rug Pull gang and used it as a blacklist to screen out the set of victim addresses from the transaction records of the liquidity pool corresponding to the Rug Pull token.
After analyzing these victim addresses, we obtained the victim address information associated with the fund retention address (Table 7) and the contract call information of the victim address (Table 8).
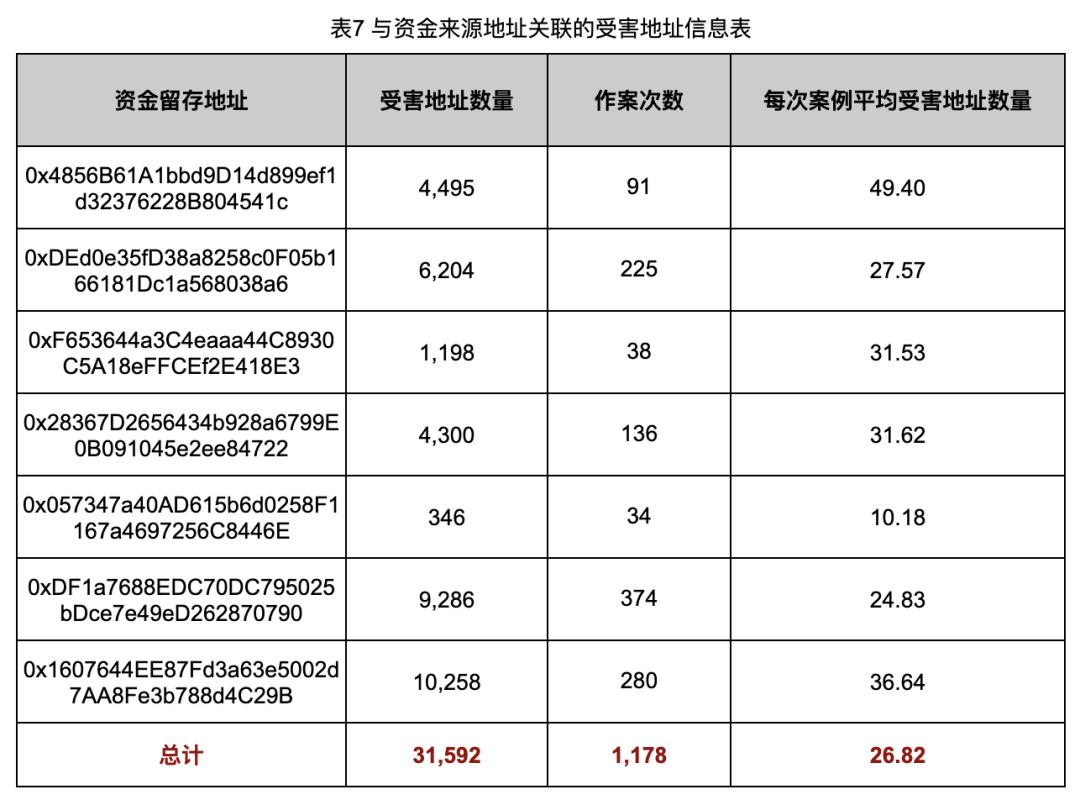
As can be seen from the data in Table 7, among the Rug Pull cases captured by the on-chain monitoring system (CertiK Alert) we analyzed, the average number of victim addresses per case was 26.82. This number is actually higher than we originally expected, which also means that these rug pull cases cause more harm than we previously thought.
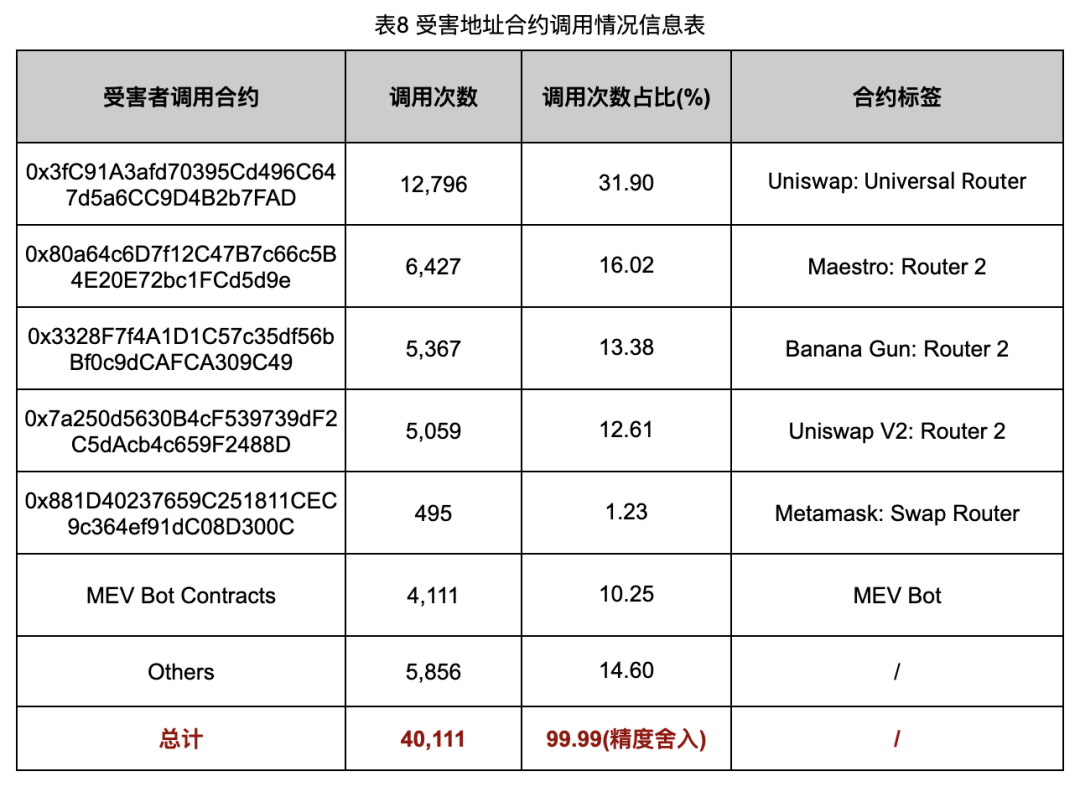
It can be seen from the data in Table 8 that in the contract calls of the victim address to purchase Rug Pull tokens, in addition to more conventional purchase methods such as Uniswap and MetaMask Swap, 30.40% of Rug Pull tokens were purchased through Maestro Purchased from well-known on-chain sniper robot platforms such as Banana Gun.
This discovery reminds us that on-chain sniper robots may be one of the important promotion channels for the Rug Pull gang. Through these sniper robots, the Rug Pull gang can quickly attract participants, especially those who focus on token hunting. Therefore, we focus our attention on these on-chain sniper bots to further understand their role in Rug Pull scams and their promotion mechanisms.
Rug Pull Token Promotion Channel
We investigated the current Web3 new ecosystem, studied the operation mode of on-chain sniper robots, and combined with certain social engineering methods, finally locked in two possible Rug Pull gang advertising channels: Twitter and Telegram groups.
It should be emphasized that these Twitter and Telegram groups were not specially created by the Rug Pull group, but existed as basic components in the new ecosystem. They are maintained by third-party organizations such as the on-chain sniper robot operation team or the professional innovator team, and are dedicated to pushing newly launched tokens to innovators. These groups have become a natural advertising channel for the Rug Pull gang, attracting users to purchase malicious tokens by pushing new tokens, thereby committing fraud.
· Twitter advertising
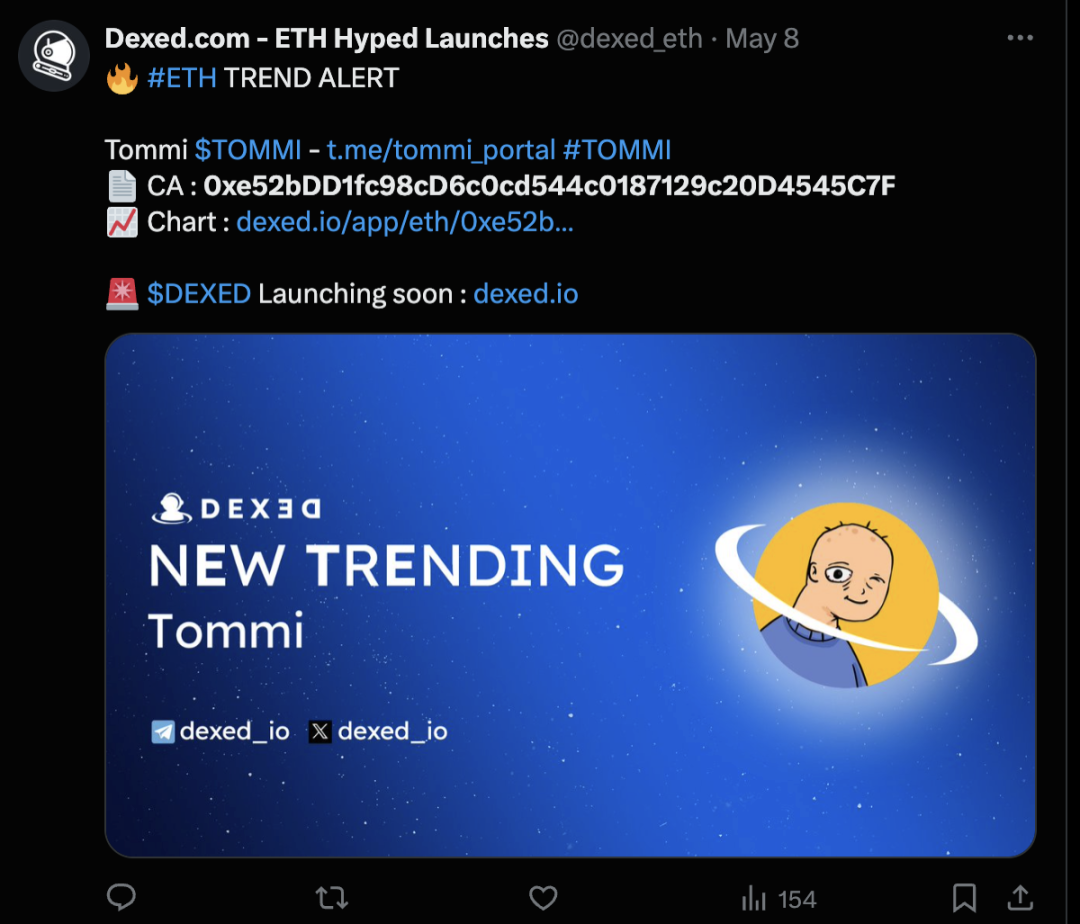
Figure 15 Twitter advertisement of TOMMI token
Figure 15 shows the advertisement of the TOMMI token mentioned above on Twitter. It can be seen that the Rug Pull gang used Dexed.com’s new currency push service to expose its Rug Pull tokens to the outside world in order to attract more victims. In actual research, we found that a considerable number of Rug Pull tokens can find their corresponding advertisements on Twitter, and these advertisements often come from the Twitter accounts of different third-party organizations.
· Telegram group ads
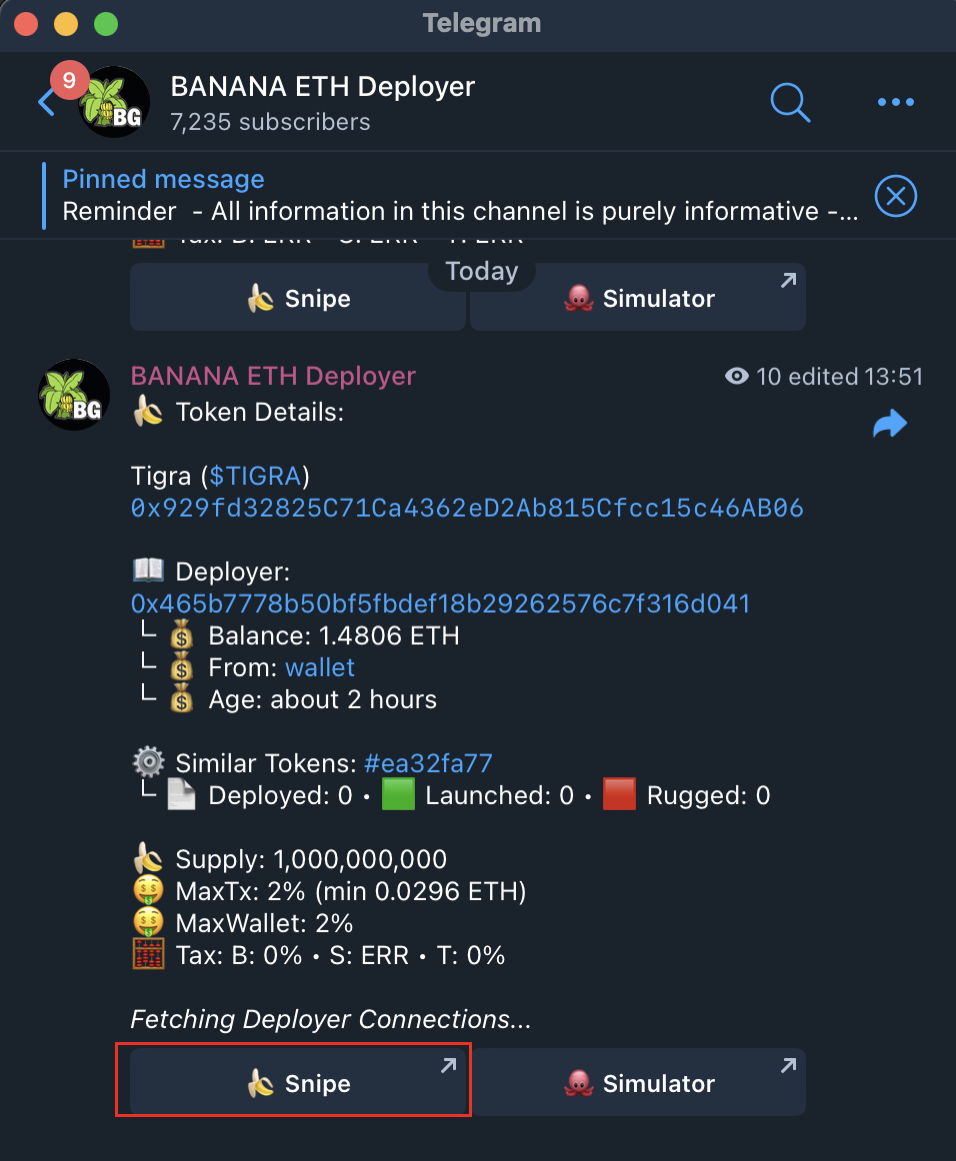
Figure 16 Banana Gun new currency push group
Figure 16 shows the Telegram group maintained by the on-chain sniper robot Banana Gun team specifically for pushing newly launched tokens. This group not only pushes basic information about new tokens, but also provides users with a convenient purchase entrance. After the user configures the basic settings of Banana Gun Sniper Bot, click the "Snipe" button corresponding to the token push information in the group (red box in Figure 16) to quickly purchase the token.
We conducted manual inspection of the tokens pushed in this group and found that a large proportion of the tokens were Rug Pull tokens. This discovery further deepens our speculation that Telegram groups are likely to be an important advertising channel for the Rug Pull gang.
The question now is, what proportion of the new tokens pushed by third-party institutions are Rug Pull tokens? What is the scale of these Rug Pull gangs' crimes? In order to clarify these issues, we decided to conduct a systematic scan and analysis of the new token data pushed in the Telegram group to reveal the scale of the risk behind it and the influence of the fraud.
Ethereum Token Ecological Analysis
· Analyze tokens pushed in Telegram groups
In order to study the Rug Pull proportion of new tokens pushed in these Telegram groups, we crawled Banana Gun, Unibot and other third-party Token message groups through Telegram’s API between October 2023 and August 2024. Pushed Ethereum new token information, it was found that these groups pushed a total of 93,930 tokens during this period.
According to our analysis of the Rug Pull case, the Rug Pull gang usually uses Rug Pull tokens to create a liquidity pool in Uniswap V2 and invests a certain amount of ETH when committing crimes. After a user or a new robot purchases Rug Pull tokens in the pool, the attacker makes a profit by destroying the market or removing liquidity. The entire process usually ends within 24 hours.
Therefore, we summarized the following detection rules for Rug Pull tokens and used these rules to scan these 93,930 tokens with the purpose of determining the proportion of Rug Pull tokens among the new tokens pushed in these Telegram groups:
1. There has been no transfer of the target token in the past 24 hours: Rug Pull tokens usually no longer have any activity after the sell-off is completed;
2. There is a liquidity pool for the target token and ETH in Uniswap V2: The Rug Pull group will create a liquidity pool for the token and ETH in Uniswap V2;
3. The total number of Transfer events since the creation of the token to the time of detection does not exceed 1,000: Rug Pull tokens generally have fewer transactions, so the number of transfers is relatively small;
4. There was a large amount of liquidity pool withdrawal or selling behavior in the last 5 transactions involving the token: The Rug Pull token will undergo a large amount of liquidity withdrawal or selling behavior at the end of the scam.
These rules were used to detect the tokens pushed by the Telegram group, and the results are shown in Table 10.
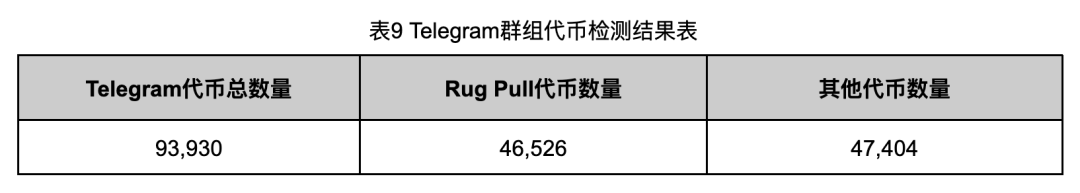
As shown in Table 9, among the 93,930 tokens pushed by the Telegram group, a total of 46,526 Rug Pull tokens were detected, accounting for 49.53%. This means that almost half of the tokens pushed in the Telegram group are Rug Pull tokens.
Considering that some project parties will also withdraw liquidity after the project fails, this behavior should not be simply classified as the Rug Pull fraud mentioned in this article. Therefore, we need to consider the impact of false positives that this situation may cause on the results of this article's analysis. Although Article 3 of our detection rules has been able to filter out most similar situations, misjudgments may still exist.
In order to better understand the impact of these potential false positives, we conducted statistics on the active time of these 46,526 tokens that were detected as Rug Pulls. The results are shown in Table 10. By analyzing the active time of these tokens, we can further distinguish between true Rug Pull behavior and liquidity withdrawal behavior due to project failure, thereby making a more accurate assessment of the actual scale of Rug Pull.
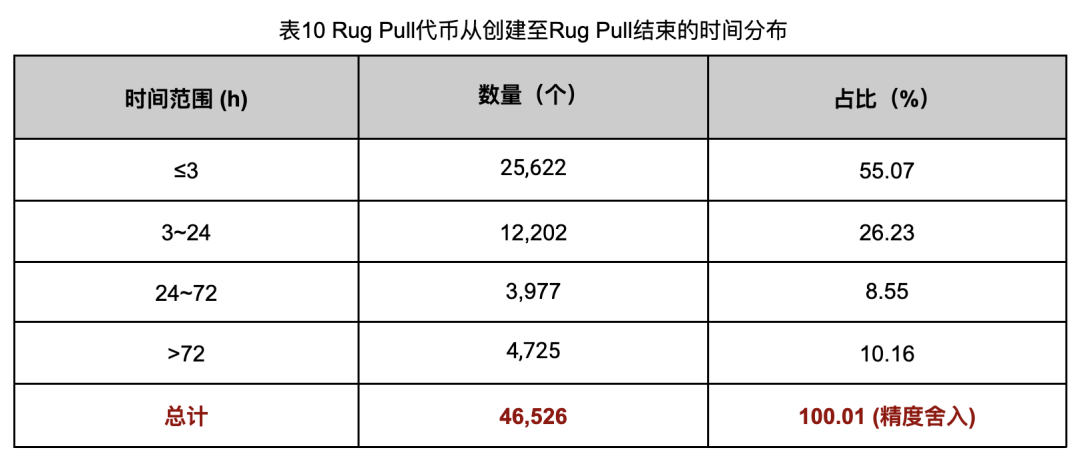
Through the statistics of active time, we found that the active time of 41,801 Rug Pull tokens (the time from token creation to the final execution of Rug Pull) is less than 72 hours, accounting for 89.84%. Under normal circumstances, 72 hours is not enough time to judge whether a project has failed. Therefore, this article believes that the Rug Pull behavior that is active for less than 72 hours is not a normal behavior of the project party to withdraw funds.
Therefore, even in the least ideal situation, the remaining 4,725 Rug Pull tokens with active time greater than 72 hours do not belong to the Rug Pull fraud cases defined in this article, our analysis still has a high reference value, because there are still 89.84% of the cases met expectations. In fact, the 72-hour time setting is still relatively conservative, because in actual sampling testing, a considerable part of the tokens that have been active for more than 72 hours still fall into the Rug Pull fraud category mentioned in this article.
It is worth mentioning that the number of tokens active for less than 3 hours is 25,622, accounting for 55.07%. This shows that the Rug Pull gang is committing crimes in a cycle with very high efficiency. The crime style tends to be "short, flat and fast" and the capital turnover rate is extremely high.
We also evaluated the cash-out methods and contract calling methods of these 46,526 Rug Pull token cases in order to confirm the committing crimes of these Rug Pull groups.
The evaluation of cash-out methods mainly counts the number of cases corresponding to the various methods used by the Rug Pull group to obtain ETH from the liquidity pool. The main methods are:
1. Smashing: The Rug Pull gang uses tokens obtained through pre-allocation or code backdoors to redeem all ETH in the liquidity pool.
2. Removing liquidity: The Rug Pull group withdraws all the funds they originally added to the liquidity pool.
The evaluation of the contract calling method is to check the target contract object called by the Rug Pull team when executing Rug Pull. The main objects are:
1. Decentralized exchange Router contract: used to directly operate liquidity.
2. The attack contract built by the Rug Pull gang: a custom contract used to perform complex fraud operations.
By evaluating the cash-out methods and contract calling methods, we can further understand the operating modes and characteristics of the Rug Pull gang, so as to better prevent and identify similar fraud behaviors.
The relevant evaluation data of the cash-out method is shown in Table 11.
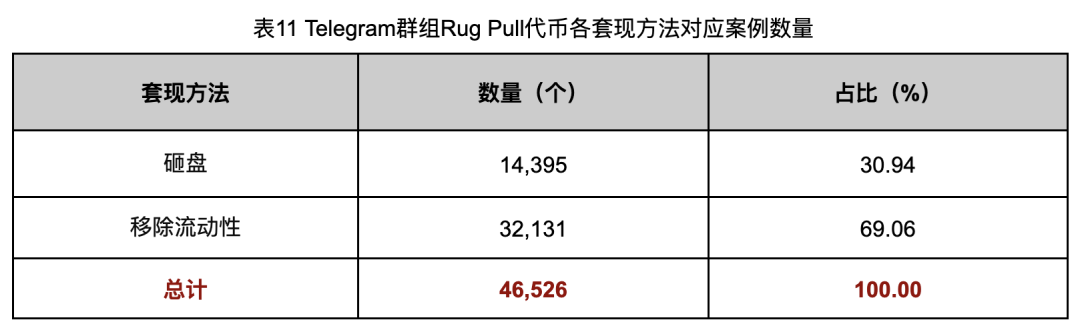
It can be seen from the evaluation data that the number of cases in which the Rug Pull group cashed out by removing liquidity was 32,131, accounting for 69.06%. This shows that these Rug Pull groups are more inclined to cash out by removing liquidity. The possible reason is that this method is simpler and more direct and does not require complex contract writing or additional operations. In contrast, the method of cashing out through selling requires the Rug Pull gang to pre-set a backdoor in the contract code of the token, allowing them to obtain the tokens required for selling at zero cost. This operation process is cumbersome and may increase risks. , so there are relatively few cases choosing this method.
The relevant evaluation data of the contract calling method is shown in Table 12.
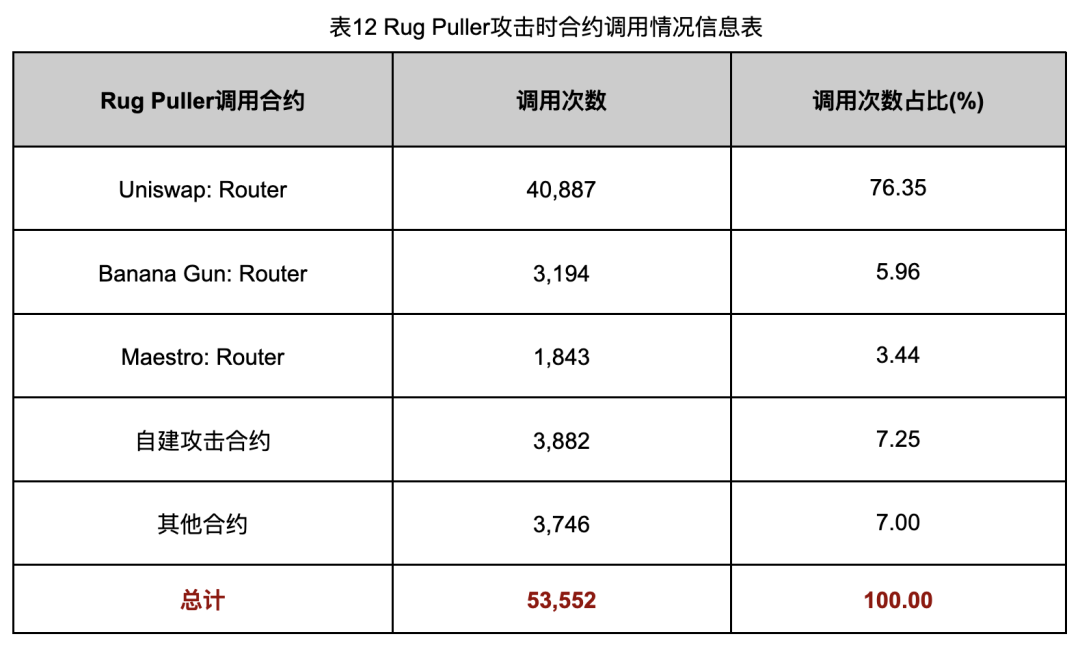
It can be clearly seen from the data in Table 12 that the Rug Pull group prefers to perform Rug Pull operations through Uniswap’s Router contract, and has performed a total of 40,887 times, accounting for 76.35% of the total number of executions. The total number of Rug Pull executions is 53,552, which is higher than the number of Rug Pull tokens, 46,526. This shows that in some cases, the Rug Pull gang will perform multiple Rug Pull operations, possibly to maximize profits or target different victims. Cash out in batches.
Next, we conducted a statistical analysis of the cost and benefit data of 46,526 Rug Pull cases. It should be noted that we regard the ETH obtained by the Rug Pull group from the centralized exchange or flash exchange service before deploying the token as a cost, and the ETH recovered during the final Rug Pull is treated as income for relevant statistics. . Since the ETH invested by some of the Rug Pull gangs themselves when forging the liquidity pool transaction volume is not taken into account, the actual cost data may be higher.
Cost and benefit data are shown in Table 13.
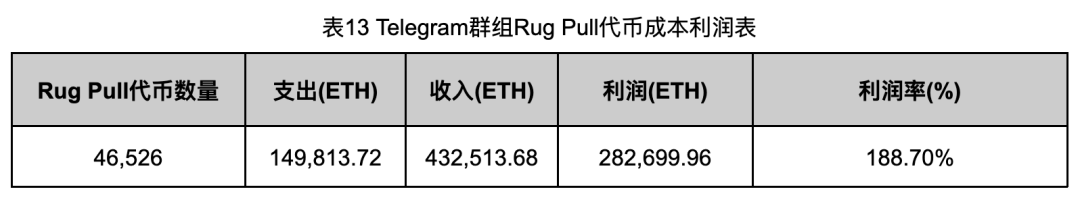
In the statistics of these 46,526 Rug Pull tokens, the final total profit was 282,699.96 ETH, with a profit margin as high as 188.70%, equivalent to approximately US$800 million. Although the actual profit may be slightly lower than the above data, the overall scale of funds is still very amazing, showing that these Rug Pull gangs have obtained huge profits through fraud.
Judging from the token data analysis of the entire Telegram group, the current Ethereum ecosystem is already filled with a large number of Rug Pull tokens. However, we still need to confirm an important question: Do the tokens pushed in these Telegram groups cover all tokens launched on the Ethereum mainnet? If not, what percentage do they account for among the tokens launched on the Ethereum mainnet?
Answering this question will give us a comprehensive understanding of the current Ethereum token ecosystem. Therefore, we began to conduct an in-depth analysis of the tokens on the Ethereum mainnet to determine the coverage of tokens pushed by the Telegram group among the entire mainnet tokens. Through this analysis, we can further clarify the severity of the Rug Pull problem in the entire Ethereum ecosystem, as well as the influence of these Telegram groups in token push and promotion.
· Analysis of tokens issued by Ethereum main network
We crawled the block data of the same time period (October 2023) from the RPC node as the above analysis Telegram group token information (October 2023 to August 2024). Token that realizes business logic by agent, because the tokens deployed by proxy are very few cases involving Rug Pull). The number of tokens caught in the end is 154,500, of which the number of tokens (LP) tokens of the Uniswap V2 is 54,240, while the LP tokens are not within the observation range of this article.
Therefore, we filtered the LP token, and the number of token we got was 100,260. The relevant information is shown in Table 14.

We conducted the Rug Pull rules for the 100,260s, and the results were shown in Table 15.
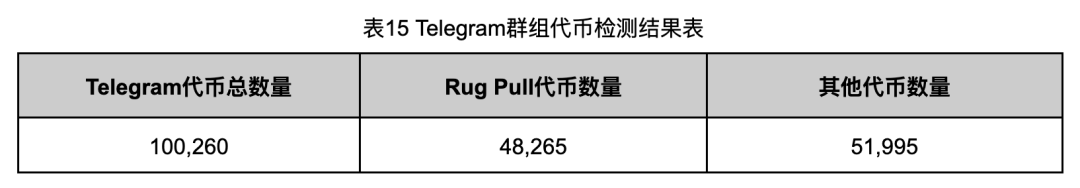
In the 100,260s token detected by Rug Pull, we found that 48,265 token to tokens were found, accounting for 48.14%of the total. Roughly equivalent.
In order to further analyze the relationship between the tokens pushed by the Telegram group and all the tokens of the Ethereum online, we have compared the information of these two sets of tokens in detail, and the results are shown in Table 16.
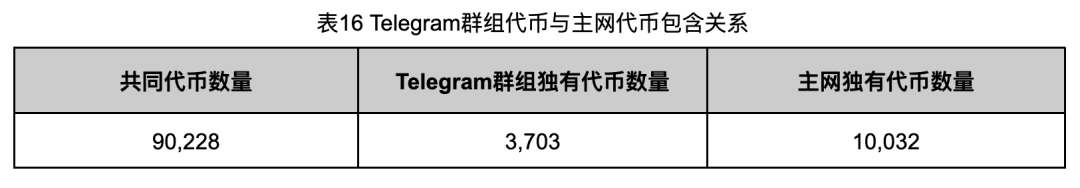
From the data in Table 16, it can be seen that there are 90,228 intersections between the tokens pushed by the Telegram group and the tokens captured by the main network, accounting for 89.99%of the main network token. And 3,703 tokens in the Telegram group are not included in the tokens captured by the main network. After sampling testing, these tokens are tokens. Token to achieve agency.
As for 10,032 tokens pushed by the Telegram group in the main network token, the reason may be that these tokens were filtered by the push rules of the Telegram group. Do not meet certain push standards.
In order to further analyze, we alone conducted the Rug Pull test of these 3,703 tokens that achieved contract agents, and finally found only 10 Rug Pull tokens. Therefore, these contract agent tokens did not cause much interference to the RUG PULL test results of the Telegram group in the Telegram group, which indicates that the tokens pushed by the Telegram group and the Rug Pull test results of the GDB tokens are highly consistent.
These 10 agents of the Rug Pull tokens are listed in Table 17. If you are interested, you can check the relevant details of these addresses. This article will not be further expanded here.
Through this analysis, we confirm that the tokens pushed by the Telegram group have a high degree of coincidence with the main network token in the Rug Pull token ratio, further verifying the importance and impact of these push channels in the current Rug Pull ecosystem force.

Now we can answer this question, whether the tokens pushed by the Telegram group cover all the tokens that Ethereum are online, and how much do they occupy?
The answer is that the tokens pushed by the Telegram group account for about 90%of the main network, and its Rug Pull test results are highly consistent with the Rug Pull test results of the main network token. Therefore, the Rug Pull detection and data analysis of the Telegram group pushed the tokens for the Telegram group can basically reflect the current status of the tokens of the Ethereum main network.
As mentioned earlier, the Rug Pull tokens on the Ethereum main network account for about 48.14%, but we are also interested in the remaining 51.86%non -Rug Pull tokens. Even if the Rug PULL tokens are excluded, 51,995 tokens are still unknown, and this number far exceeds our expectations of reasonable tokens. Therefore, we have statistics from all the tokens on the main network from creation to the end, and the results are shown in Table 18.
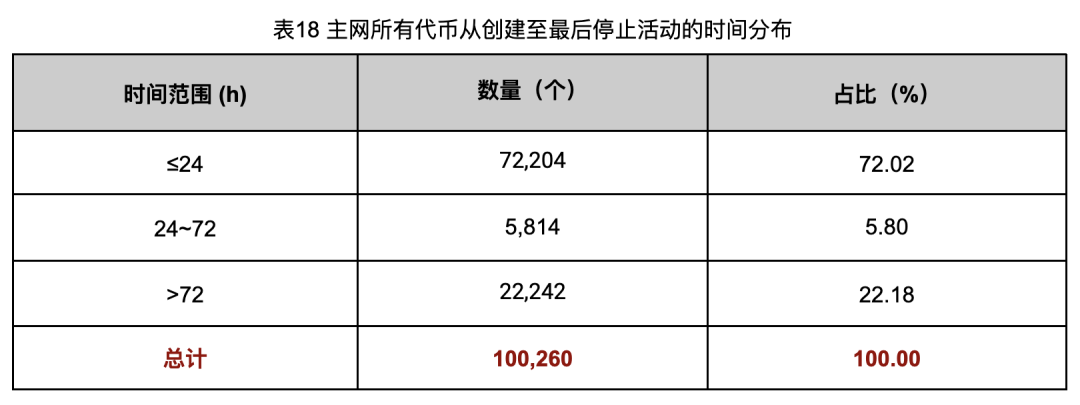
From the data in Table 18, we can see that when we extend the field of vision to the entire Ethereum main network, the number of tokens with a token life cycle of less than 72 hours will be 78,018, accounting for 77.82%of the total. This number is significantly higher than the number of Rug Pull token we detected. This shows that the Rug Pull detection rules mentioned in this article cannot completely cover all Rug Pull cases. In fact, through sampling testing, we did find that there were unlocked Rug Pull tokens. At the same time, this may also mean that there are some other fraud forms that have not been covered, such as fishing attacks, puppets, etc. These still require us to further dig and explore.
In addition, the number of tokens with a life cycle of more than 72 hours is as high as 22,242. However, this token is not the key excavation object of this article, so there may still be other details waiting to be discovered. Perhaps some of the tokens represent failed projects, or items that have a certain user base but failed to obtain long -term development support. The stories and reasons behind these tokens may hide more complex market developments.
The tokens of the Ethereum main network are much more complicated than what we think in advance. Various short -term and long -term projects are intertwined, and potential fraud behavior is endless. This article is mainly to attract everyone's attention. I hope everyone can realize that in our unknown corner, criminals have been acting quietly. We hope that through such an analysis, we will attract more people to pay attention and research to improve the security of the entire blockchain ecosystem.
think
Among the newly issued tokens on the Ethereum main online, the Rug Pull tokens accounted for 48.14%, which is very warning. It means that on Ethereum, there are two tokens on average, one of which is used for fraud, which reflects the current chaos and disorder of the Ethereum ecology to some extent. However, the current situation of the Ethereum token ecosystem is truly worrying. We found that in the Rug Pull case captured on the chain, the number of other blockchain networks is even more than Ethereum. So what exactly is the tokens of other networks? It is also worth further research.
In addition, even though except for the Rug Pull tokens, which accounted for 48.14%of the 48.14%, Ethereum still has about 140 new token every day. The daily distribution scope is still much higher than the reasonable range. The secret that has not been revealed? These issues are worthy of our in -depth thinking and research.
At the same time, there are many key points that need to be discussed in this article:
1. How to quickly and efficiently determine the number of Rug Pull gangs in the Ethereum ecology and contact?
For a large number of Rug Pull cases currently detected, how to effectively determine how many independent Rug Pull gangs are hidden behind these cases, and is there a connection between these gangs? This analysis may need to combine the flow of funds and the address of the address.
2. How to accurately distinguish the victim 's address and attacker address in the Rug PULL case?
The distinction of victims and attackers is an important step in identifying fraud. However, the boundaries between the victim's address and the attacker address are blurred in many cases. How to distinguish more accurately is a question worthy of in -depth research.
3. How to move the Rug PULL test before or even beforehand?
The current RUG PULL detection method is mainly based on post -after -after analysis. Can it develop a method of incident or pre -detection to identify the Rug Pull risks that may exist in the current active tokens in advance? This ability will help reduce investors' losses and intervene in time.
4. What is the profit strategy of the Rug PULL gang?
Study what kind of profit conditions of the Rug Pull gang will perform RUG PULL (for example, choose to run the way when the average profit is made, please refer to part 13 in this article), and whether they use certain mechanisms or means to ensure their profits . This information helps predict the occurrence of Rug Pull behavior and strengthen prevention.
5. In addition to Twitter and Telegram, are there any other promotional channels?
The Rug Pull gang mentioned in this article mainly promotes its fraud token through channels such as Twitter and Telegram, but is there any other promotion channels that may be used? For example, forums, social media, advertising platforms, etc. Is there similar risks in these channels?
These issues are worthy of our in -depth discussion and thinking. It will no longer start here, leaving as everyone's research and discussion. The rapid development of the web3 ecology is that the security not only depends on the advancement of technology, but also requires more comprehensive monitoring and in -depth research to cope with changing risks and challenges.
suggestion
As mentioned earlier, the current tokens are full of scams in the new ecosystem. As a web3 investor, if you care about it, you may suffer losses. With the increasingly upgraded offensive and defensive confrontation between the Rug Pull gang and the anti -fraud team, investors' difficulty in identifying fraud tokens or projects is also increasing.
Therefore, for investors who want to contact the new market, our team of security experts provides the following suggestions for reference:
1. Try to purchase new tokens through well -known centralized exchanges: prioritize the selection of well -known centralized exchanges for purchase of new tokens. These platforms are more strict in project review and relatively high security.
2. When purchasing the new tokens through the decentralized exchange, you need to recognize the official website and the address of the chain: to ensure that the tokens purchased are from the official contract address issued to avoid buying fraud token by mistake.
3. Before purchasing the new tokens, verify whether the project has the official website and the community: there are often high risks without official website or active communities. In particular, pay attention to the new tokens pushed by third -party Twitter and Telegram groups. Most of these pushes have not been verified by security.
4. View the creation time of the tokens to avoid buying tokens with a creation time of less than 3 days: if you have a certain technical foundation, you can view the creation time of the tokens through the block browser, and try to avoid buying a generation that has just been created for less than 3 days. Coins, because the active time of the Rug Pull tokens is usually short.
5. Use the tokens scan service of third -party security institutions: If conditions permit, you can use the token scanning services provided by third -party security institutions to detect the security of the target token.
call
In addition to the Rug Pull scam gang focusing on this article, more and more illegal criminals are using the infrastructure and mechanism of various fields or platforms in the web3 industry to make illegal profits, making the current Web3 ecosystem's security status increasingly serious. We need to start paying attention to some issues that are easy to ignore, so as not to let the criminals be organic.
As mentioned earlier, the inflow and outflow of the Rug Pull gang will eventually flow through the major exchanges, but we think that the capital flow of Rug Pull fraud is only the corner of the iceberg, and the scale of malicious funds flowing through the exchange may far exceed our imagination. Therefore, we strongly call on major exchanges to adopt stricter regulatory measures for these malicious capital flows to actively crack down on illegal fraud to ensure the security of users' funds.
Similar to third -party service providers such as project promotion and chain sniper BOT, its infrastructure has actually become a tool for fraud gangs to make a profit. Therefore, we call on all third -party service providers to strengthen the safety review of products or content to avoid malicious use of criminals.
At the same time, we also call on all the victims, including the MEV arbitrage and ordinary users, to actively use the safety scanning tool test target project, refer to the project rating of the authoritative security institution, and actively disclose the malicious behavior of the criminals. Exposing the illegal phenomenon in the industry.
As a professional security team, we also call on all security practitioners to actively discover, screen, and fight against illegal behaviors, diligently speak, and escort the user's property security.
In the field of Web3, third -party service providers such as users, project parties, exchanges, MEV arbitrage, and BOT play a vital role. We hope that every participant can contribute to the sustainable development of the web3 ecology and create a safer and transparent blockchain environment.


 chaincatcher
chaincatcher