Interpretation of Story White Paper: A peer-to-peer intellectual property network

Reprinted from panewslab
02/07/2025·17Dsummary
Story, a peer-to-peer intellectual property network, is committed to building the world's first programmable knowledge and creativity market. In Story, scientific and creative assets can be registered in a common ledger with custom parameters. All assets have standardized interfaces and can be used by any software application or artificial intelligence model to realize the free circulation and value realization of intellectual property rights. Story coordinates assets through a decentralized network map: nodes represent independent intellectual property assets, while edges represent legal and economic commitments of the asset. Story also has an asynchronous and decentralized verification mechanism to evaluate the uniqueness of assets based on crypto-economic incentives to ensure fairness and transparency. Join Story to help grow the world’s only, open, license-free repository of knowledge and creativity.
1. Introduction
The current intellectual property (IP) system relies heavily on centralized institutions to manage ownership and value circulation. From social media to pharmaceutical companies, a few unregulated institutions have firm control over the production and exchange of knowledge globally, which has led to the high cost of IP transactions. What's worse is that traditional IP systems are difficult to cope with the large-scale generation and distribution of content in the AI era. The works of individual creators are captured, trained, and utilized by AI without permission, but are not signed or rewarded; while AI companies cannot sign authorization agreements for massive content one by one, and the IP market lacks transparency and liquidity.
We need a truly open, programmable peer-to-peer intellectual property market that allows anyone to freely create, trade and cash out, and avoid exploitation from monopoly institutions. In Story, each IP asset has programmable authorization rules embedded in it that can be monetized and traded on any application. Story not only provides a global IP repository, but also provides a programmable IP market that drives exponential growth in human knowledge productivity.
2. Architecture Overview
The development of blockchain technology has gone through multiple stages. Bitcoin [1] introduced decentralized ledgers for the first time, and Ethereum [2] built a smart contract platform on this basis, giving birth to new asset classes such as NFT. Subsequently, blockchain faces the challenge of scalability, and high-performance public chains such as Solana[3] emerged to try to break through restrictions. Although the industry has long focused on balancing the "triple difficulties" of blockchain decentralization, scalability and security, the applicability and availability of blockchain have been ignored, which has become the mainstream path to adopt blockchain technology. Obstacles on. Therefore, we need a new type of blockchain that not only solves technical challenges, but also creates a programmable market for complex new assets, so that blockchain technology can truly serve the real world.
Story is a specially designed decentralized blockchain equipped with a multi-core execution environment. It consists of a main execution core and multiple highly customized cores. The main core is equivalent to an Ethereum virtual machine (EVM), which quickly adopts existing applications in the ecosystem. The Intellectual Property (IP) core is one of the dedicated cores that efficiently handle intellectual property registration as native asset classes, while also optimizing operations of complex IP relationship maps. The IP core transforms intelligence into programmable IP assets. Although Story mainly focuses on intellectual property rights, its flexible architecture allows the core application scope of the future to go far beyond the scope of IP applications.
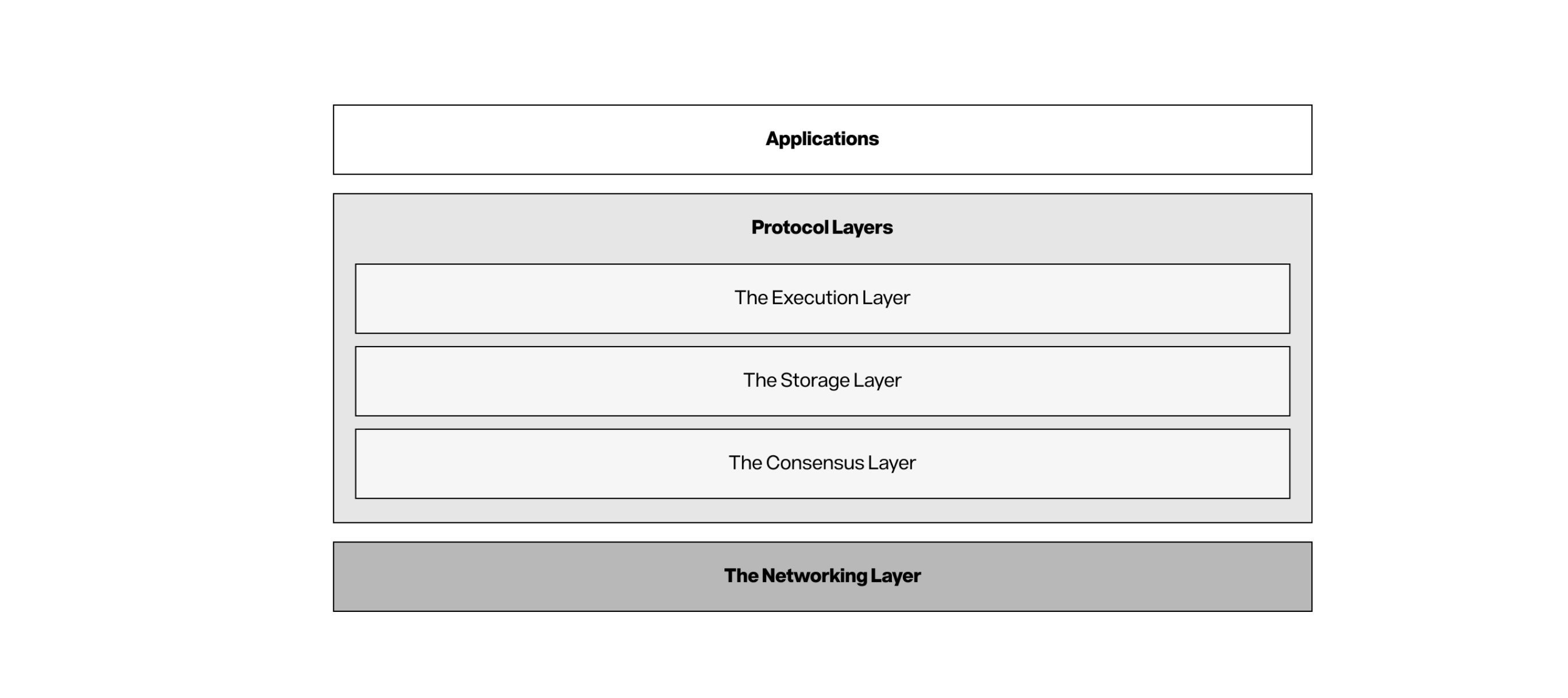
Figure 1: Story\'s protocol layer
Story runs on a set of decentralized nodes (or validators) that are connected via a point-to-point network. They work together to ensure consensus conclusion, transaction processing and chain integrity, and build a secure decentralized network where any participant who follows the protocol rules can join. Following the principle of separation of concerns, the protocol can be divided into three layers: execution layer, storage layer and consensus layer.
2.1 Execution layer
The execution layer is the computing basis of Story and is responsible for the execution of all transactions and smart contracts. It consists of a main core and multiple dedicated cores that work together. The execution layer is designed to provide maximum flexibility and computing power to each core while ensuring network stability and activity.
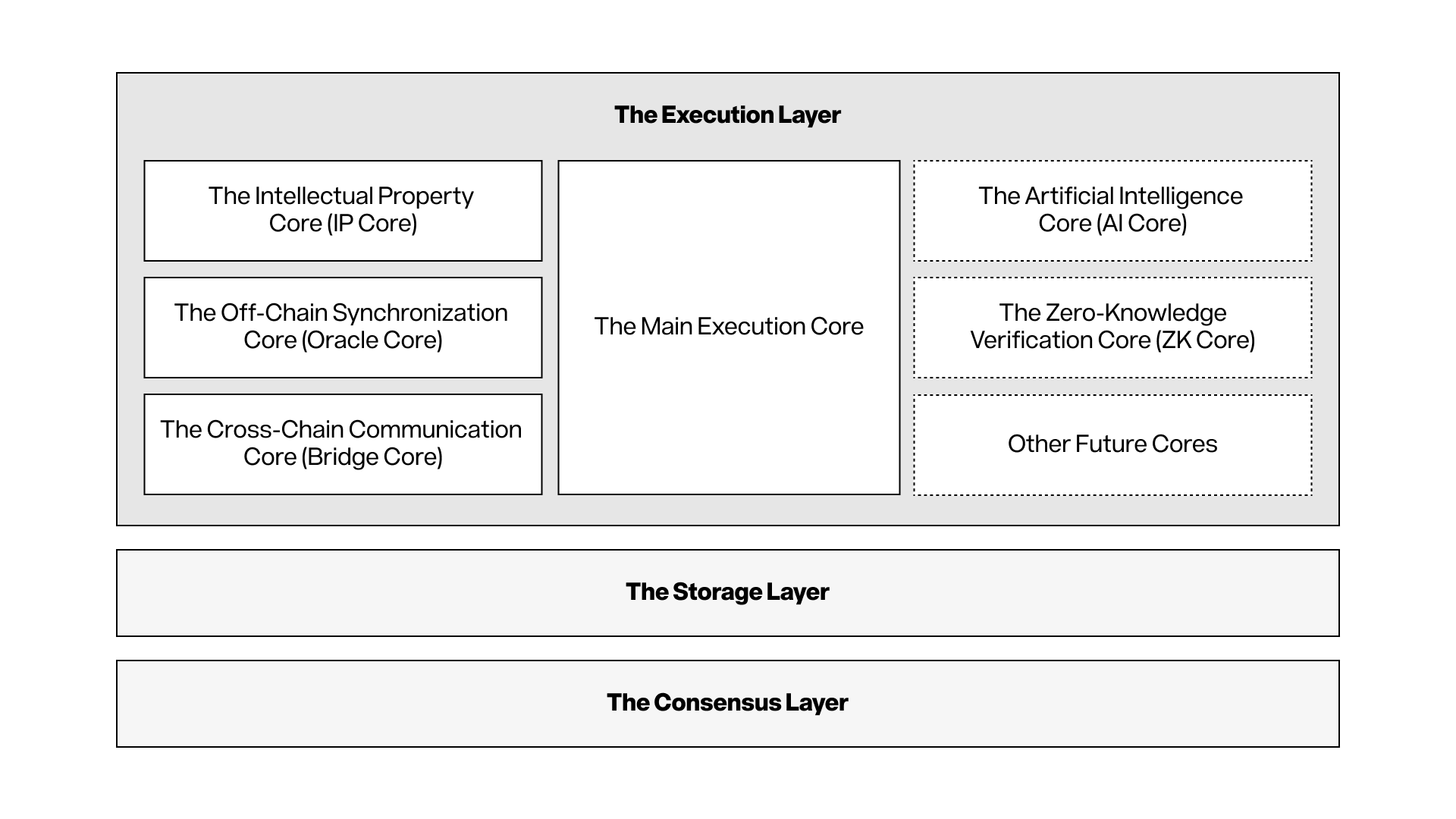
Figure 2: Multi-core design of execution layer
The main core is the default execution environment and is fully compatible with EVM. The main core processes all transactions. When the transaction call involves the corresponding dedicated core contract, the main core can activate the corresponding dedicated core. The execution environment for each dedicated core is optimized and prioritizes specific needs such as processing speed, scalability, security, or privacy. For example, the way data is modeled, stored and processed in some applications directly affects its scalability and even feasibility. The complexity of multi-core design is invisible to users, as each dedicated core provides functionality through smart contracts that is automatically activated when the user interacts with the relevant contract. All cores follow the following requirements:
-
Determinism: The execution result of any method call must be deterministic. For example, while a core may use GPU internally to accelerate floating point calculations, the end result must be consistent. Non-deterministic behaviors threaten the stability and activity of the network.
-
Limited and measurable resource consumption: Each core must accurately calculate the expected resource consumption (such as gas fees) for all contract calls and calculate it according to the input parameters within a constant time. Incorrect measurement can undermine network stability and fair use.
-
Storage: Each stateful core can store data in the namespace of its storage layer in the form of key/value pairs (key/value), where data commitments are used for consensus. All key-value pairs must follow the canonical format and maintain certainty in the order of updates.
To meet different needs, Story's first release deployed three dedicated cores to work with the main core: one core is responsible for the storage and operation of IP as the native asset class, and the other core connects the on-chain execution environment with the off-chain world. Three cross-chain communication cores help IP assets circulate in the broader blockchain ecosystem.
Intellectual Property Core
In Story, intellectual property assets are presented through a multi-dimensional graph, and various types of nodes (such as IP assets, licenses, etc.) are connected through edges representing economic and legal relations. These IP Graphs track the rights, licensing and realization processes of original and derivative assets.
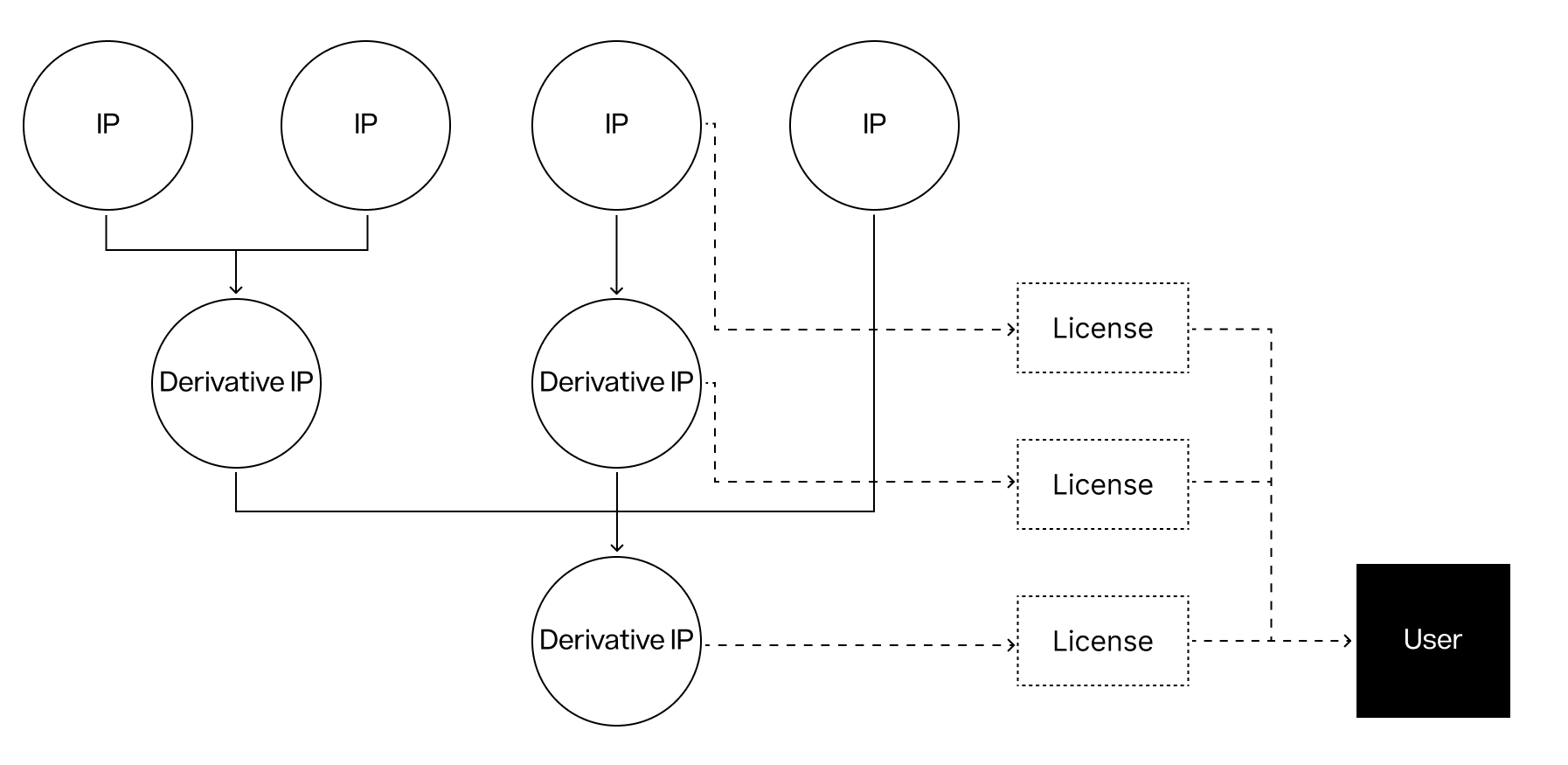
Figure 3: IP asset diagram
The PoC protocol is deployed on the IP core and is a native protocol that provides an open IP repository and a set of modules to interact with these IPs in a frictionless manner. The PoC protocol is both a standardized general ledger for IP assets on Story and a way to create a digital marketplace around these assets and their rights. The PoC protocol tracks the genealogy of IP usage, extension, and monetization in various applications, similar to Git's role in code branching and version control. This open repository makes Story the source and exchange of IP assets. layer.
IP holders can register their intellectual property on the chain and use the PoC module to customize the terms of use and copyright structure. Each intellectual property can be registered as an IP asset (ERC-721) on the chain and optionally associated with an IP account (optimized version of ERC-6551). Off-chain entities can monitor registration, verify the identity of IP holders, provide authentication for registered IPs and their licenses, and initiate a decentralized dispute handling process in the event of infringement. See Appendix A for more details on the PoC protocol.
IP core supports PoC protocols through an optimized data model, providing efficient local storage for IP-related assets, licenses, and certifications to optimize the processing of intellectual property relationship maps. This IP core also provides efficient local implementations for complex graph operations such as traversals that would otherwise take a lot of time and computational costs.
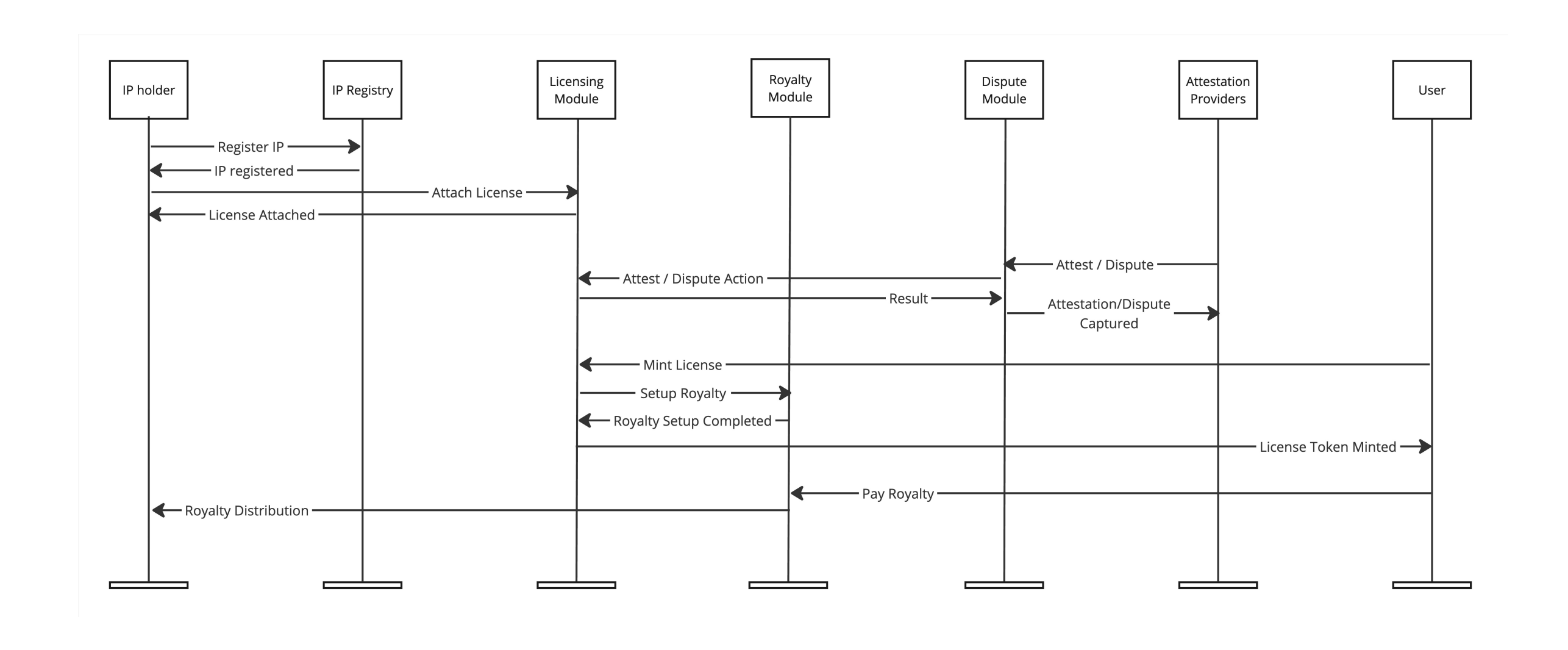
Figure 4: IP registration and use flowchart (standard process path)
For example, when a new association is established between a user and an IP asset, the protocol needs to verify compatibility by checking the IP parameters and all of its parent assets, thus ensuring uniform execution of the rules. The IP core adopts advanced algorithms to efficiently traverse the relationship map and apply a universal compatibility engine for IP terms. It is almost impossible to implement such a feature without a dedicated execution core.
Off-chain synchronization core
Oracles play an important role in the blockchain ecosystem, allowing these originally isolated systems to connect with real-world data and services. Without oracles, blockchains can only process on-chain data, which greatly limits their practical application. Off-chain synchronization core provides native support for the stable and seamless integration of oracles.
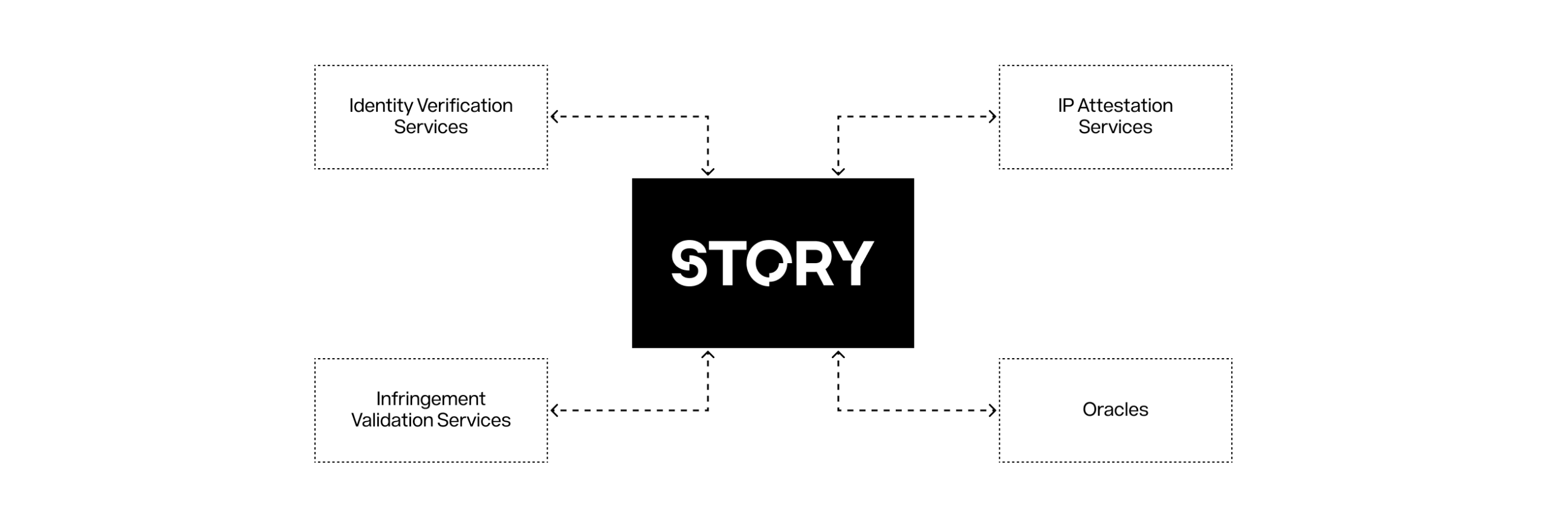
Figure 5: Off-chain synchronous core enables seamless integration of oracles and other data providers
One of the services deployed on the off-chain synchronization core is Story's Orchestration Service (SOS) framework.
The service extends the PoC agreement by verifying the authenticity of registered IP assets and licenses, verifying the creator's social identity, receiving off-chain payments and generating off-chain legal contracts available. Through an off-chain entity network, the SOS framework bridges the gap between off-chain reality and on-chain world that provide proof of basic services on Story.
Cross-chain communication core
The cross-chain communication core provides basic components for efficient cross-chain messaging. Taking the Inter-Blockchain Communication Protocol (IBC) [4] as an example, because the computational cost of verification proof (such as Merkle proof) and signature verification is too high, it becomes impractical to implement the protocol using EVM smart contracts, and this The problem is solved through the core of cross-chain communication.
The ability to support cross-chain communications promotes widespread interoperability of the ecosystem, eliminates value silos, and expands more application scenarios. For example, IP holders can use their IP assets on different blockchains to access various markets, platforms and services while ensuring consistency between ownership and monetization terms. Users can also use their IP assets as collateral on blockchains focused on DeFi. This interconnected approach ensures that IP ownership is executed regardless of where the assets are used, regardless of the execution environment, thus realizing the vision of Story becoming the IP layer for the entire network.
The scalability of the future core
Story's architecture supports the addition of new dedicated cores, which brings its capabilities beyond the realm of intellectual property. Let's look at two potential future cores.
Artificial Intelligence (AI) cores can optimize on-chain operations related to AI. By default, these operations are not feasible on EVM - as pointed out in the paper [5], the gas fee required for a single multiplication of two 1000 x 1000 matrices will exceed 3 billion, which Far beyond the gas limit of logical blocks. The AI core can use modern GPU processors to perform integer operations, combining deterministic fixed-point operations, quantization technology [6] and on-chain pseudo-random generators to eliminate non-deterministic problems caused by randomness and floating-point errors.
The Zero Knowledge (ZK) core enables efficient verification of zero-knowledge proofs such as ZK-SNARK. ZK-proof is an encryption method that allows the prover to prove to the verifier that he has certain knowledge or information without exposing the actual information. By providing native support for zero-knowledge proof verification and leveraging highly optimized software stacks or hardware acceleration, ZK cores have an advantage over smart contracts in reducing computational overhead and gas costs. This core is particularly important for applications that require confidential IP exchanges or large-scale verifiable IP maps. For example, it allows IP holders to prove their ownership and authenticity of IP assets without exposing sensitive information.
2.2 Storage layer
This storage layer is located above the consensus layer, providing storage APIs to the execution layer and its core. It simplifies the complexity of data organization, commits to encrypting data, and decides what database to use to manage the data. The design of the memory layer is inspired by the NAND flash conversion layer (FTL), which maps logical addresses to physical memory blocks for the purpose of optimizing write performance and extending the service life of the device. The storage layer also uses data placement strategies to balance the performance, scalability, cost, proof size and redundancy of heterogeneous storage systems. By analyzing usage patterns and access frequency, the storage layer can actively optimize the data distribution between different storage layers. The sub-storage system automatically adjusts according to the data size, access frequency and durability requirements to efficiently process various data types.
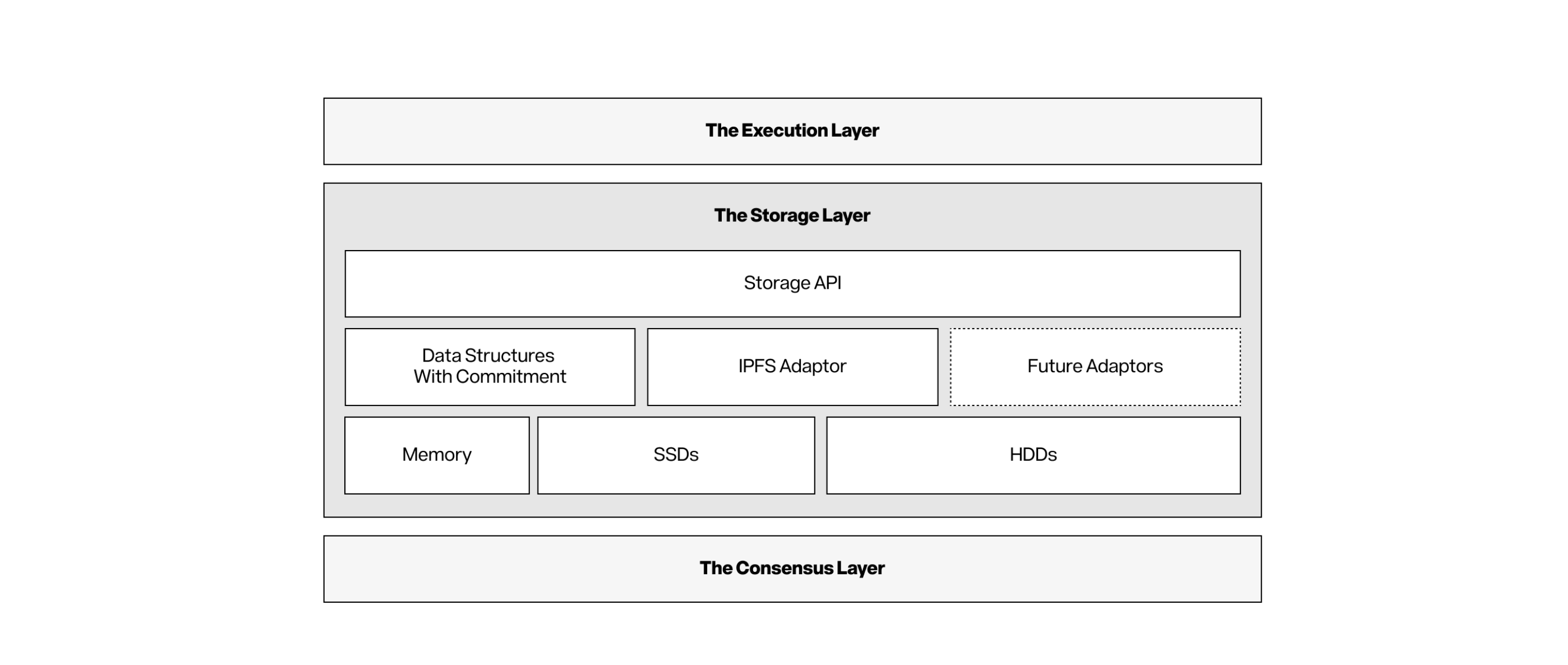
Figure 6: Story\'s storage layer
In addition to performance improvements, the storage layer also solves the fragmentation problem of user experience by providing a unified interface to integrate on-chain and off-chain storage solutions such as IPFS[7] and Arweave[8]. Intellectual property assets have various forms of expression, including small text files, large multimedia files and complex databases. The cost of storing massive data on the chain is very high. When interacting with large data sets, the traditional approach is to store content on IPFS and maintain metadata references only on-chain; this approach often has great limitations and reduces user experience. For example, when an ML model is registered as an IP asset, metadata used to capture the authenticity of the content (such as C2PA[9]) will be stored with the actual file to directly perform model inference when needed. It is worth noting that the underlying protocol has dealt with complexity, ensuring that the behavior of the interface remains certain at all times without compromising the stability of the network. The technical details will be released in the subsequent technical white paper.
2.3 Consensus layer
The consensus layer ensures network integrity, security and stability by coordinating block generation for all network participants. In recent years, the blockchain consensus mechanism has made significant breakthroughs and progress. The design of this layer is very flexible and can adapt to the addition of new consensus mechanisms.
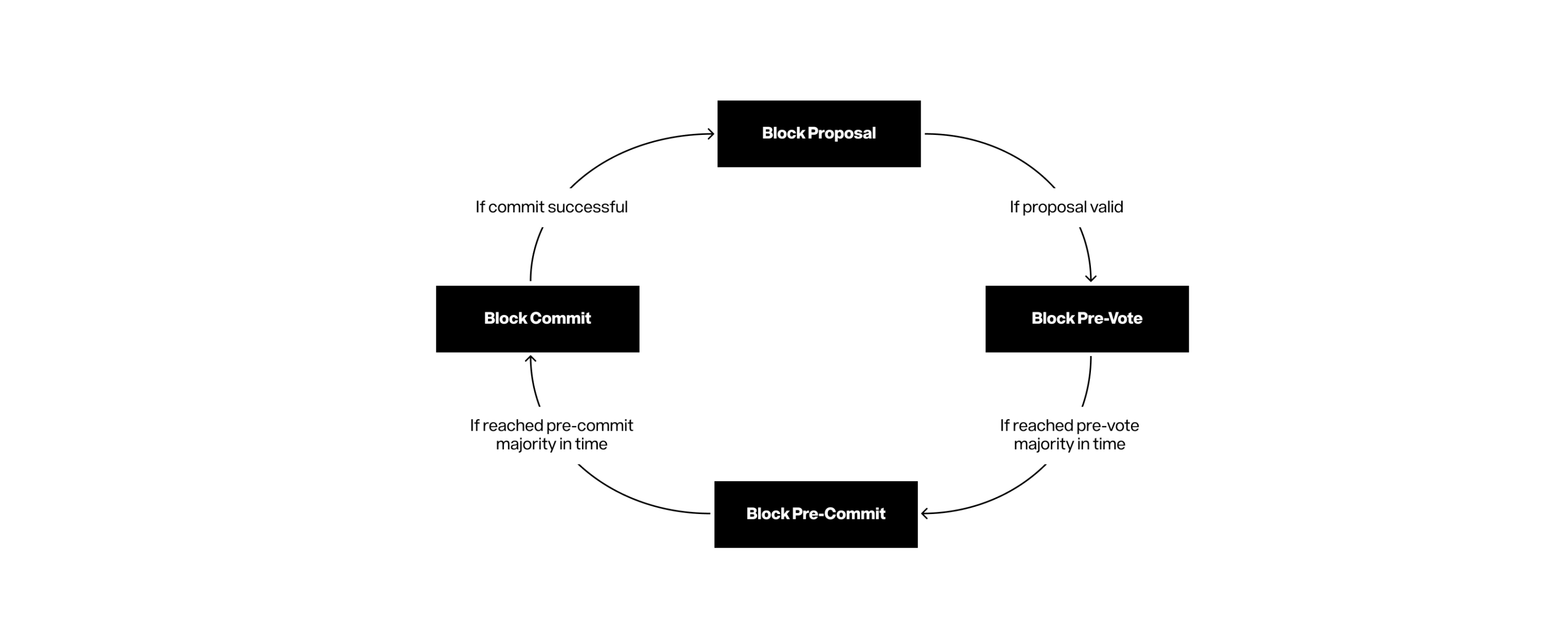
Figure 7: Block formation period of Tendermint (standard path)
Story initially adopted a modern Tendermint implementation called CometBFT. Tendermint is a Byzantine Fault Tolerance (BFT) consensus engine with clear attributes and customization options that fully meet our design needs:
-
Fault Tolerance: Even if 33% of validators commit evil or offline, the system can be kept safe. It ensures that all honest nodes reach consensus on the submitted blocks and identify and punish malicious nodes with cryptographic proof.
-
Activity Guarantee: The network continues to advance when more than two-thirds of validators (measured by voting trade-offs) remain active and participate in the network.
-
Instant Finality: The transaction can be quickly finalized after it is packaged into the block. This instant ending is crucial for applications that require immutability and directly affects the user's experience of reliability.
-
Modular design: Application Block Interface (ABCI) separates consensus and execution, ensuring that future consensus upgrades do not affect existing execution logic.
Story's consensus layer adopts a Proof of Stake (PoS) mechanism, and validators play a crucial role in maintaining the security and integrity of the blockchain. This provides financial incentives for honest and efficient operations, as malicious behavior can be punished, including losing staked tokens. This layer manages all operations related to pledge, locking requirements and reward allocation.
3. Application scenarios
In addition to Story's technical architecture, we can start thinking about the various application scenarios that a point-to-point IP system may bring. With the emergence of a common IP repository and programmable intelligence market, perhaps we are at the beginning of a new round of Renaissance. This section will explore some of the most promising application cases, and of course, there are many equally exciting applications that have not been mentioned.
3.1 The rise of the smart market
Bitcoin and Ethereum have redefined currencies over the past few decades, and outside of currency, the path to expanding blockchain to other new asset classes has been slow. The unstoppable digital market is the "killer application" of blockchain, and specially built blockchains will create a new market starting from IP.
Traditional IP systems rely too much on complex centralized structures and intermediaries, which leads to inefficiency in terms of readability, transactions and monetization of IP, an asset class with trillions of scale. The high transaction costs make it impossible for knowledge and creativity to be transformed into value, and also limit the exchange and dissemination of ideas. Story breaks the limits by supporting peer-to-peer IP transactions and programmable IPs.
Applications can integrate IP directories of pharmaceutical companies or media organizations into Story as IP RWAs (real-world assets). What is even more exciting is that native programmable IP can be combined with DeFi applications to create an emerging field - IPFi, where IP assets can be split, used as collateral, pledge or in other cost-effective ways. use.
Interaction between people is the most basic transaction in the new intelligent economy. With Story's programmable execution environment, interaction between agents and people becomes possible. Agents can automatically obtain IP assets licenses from Story and upgrade their creative style or knowledge base through fine-tuning. If income is generated, the agent can share part of the income with the original IP holder through Story's royalty module, thus forming a virtuous economic cycle that allows AI to empower IP holders rather than weaken their returns. In addition, pure IP transactions between agents and agents are also feasible. Story is used as the settlement layer of intelligent agent business to prosper the entire agent interaction market. We will detail this possibility in the next section.
3.2 The basic layer of artificial intelligence
Blockchain is the ideal foundation for AI interaction because it provides a programmable medium where software can make hard commitments. Since the agent trains with IP as native input and generates IP as native output, Story provides a basic settlement layer for AI transactions, which is suitable for training AI models and monetization of AI outputs.
Smart chain
In the AI field, intellectual property assets cover all kinds of IPs—from databases, basic ML models, to fine-tuned models and model tuning packages.
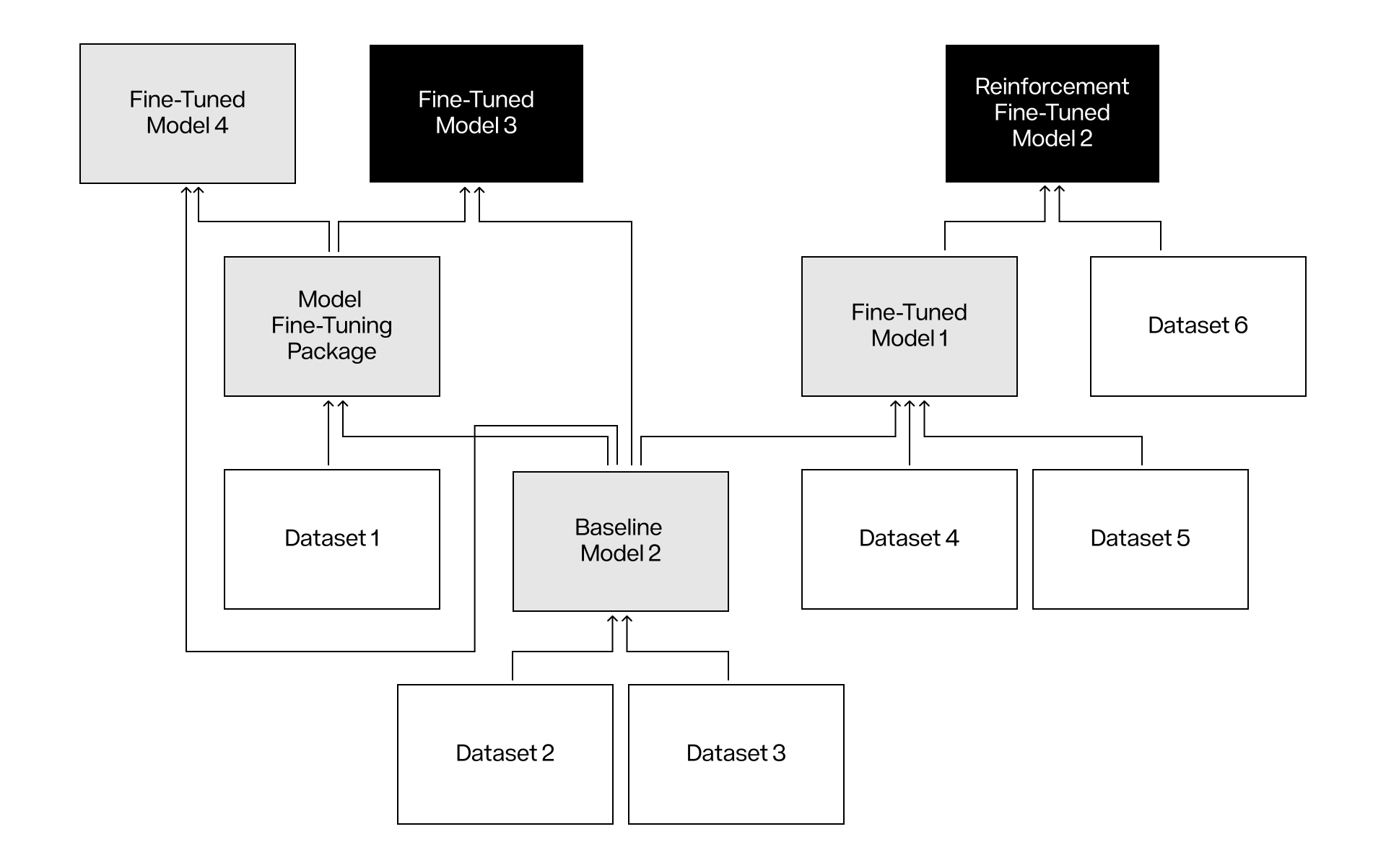
Figure 8: Schematic diagram of AI-related IP assets
Figure 8 shows how IP assets build smart chains. A machine learning model (Model 2) may come from a deep fine-tuned model (Model 1) enhanced by reinforcement learning, using other databases (Dataset 6). This fine-tuned depth model itself may originate from the underlying model trained on multiple databases. These training databases may also be a combination of other databases. In addition, research on independent model fine-tuning packages is also being actively carried out. The model fine-tuning package contains all the necessary data for efficient parametric model fine-tuning, which reduces trainable parameters while maintaining near-complete fine-tuning performance. Since comprehensive model fine-tuning requires a lot of computing resources and memory, these packages provide an efficient alternative (i.e. Huggingface Adapters). When a model is registered as an on-chain IP asset, cutting-edge model fingerprinting techniques, such as OML developed by the Sentient protocol [12], can capture the unique features and basic properties of the model.
By registering the entire smart chain on Story, the distribution of economic value among nodes in the network can be achieved. Story lays the foundation for the market for high-quality databases and model fine-tuning packages, thus driving the birth of more efficient ML models. Such incentive mechanisms encourage data providers to contribute high-quality databases and accelerate the development of AI through guaranteed and fair rewards. Under the transparent economic incentives and automated income distribution mechanism, Story becomes the negotiation, collaboration and settlement layer for seamless cooperation between data providers, model developers and end users, and ensures that all participants have reasonable ownership rights.
Smart Agent Business Model
AI is evolving from an independent model to an automated proxy network that can perceive, make and act to achieve goals. This transformation means that AI is no longer just a tool, but is gradually becoming an ecosystem where agents create value through collaborative interaction.
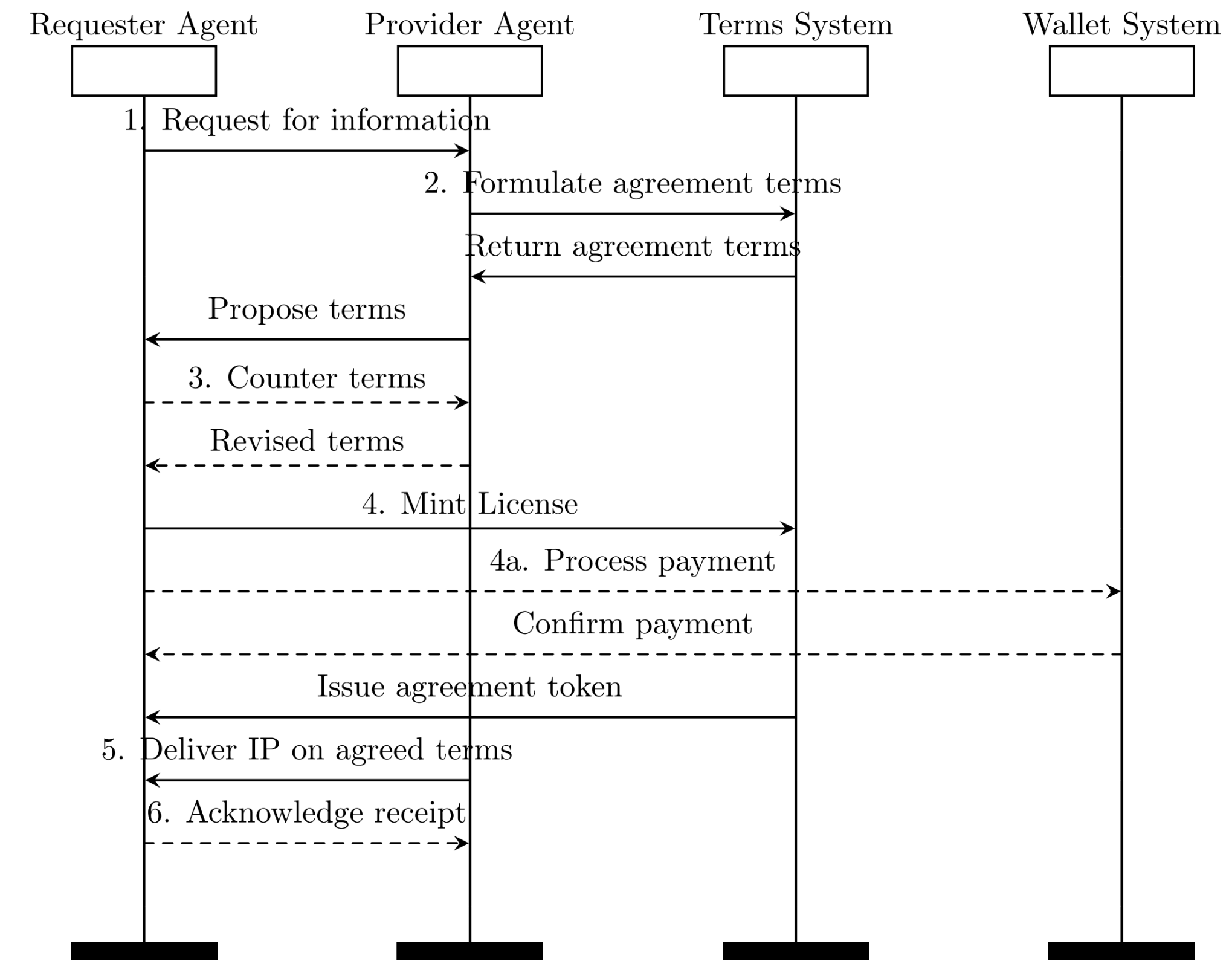
Figure 9: Agent TCP/IP protocol - Interaction process
The Agent TCP/IP protocol released by the Story team provides a key framework for the development of the automated proxy ecosystem. The purpose of designing Agent TCP/IP is to promote standardized automatic interactions between AI agents. This proxy-to-agent protocol lays the foundation for IP asset exchanges between agents (such as training data, proprietary algorithms, and creative content) without relying on manual intermediaries. With the Agent TCP/IP protocol, agents can automatically negotiate, authorize and execute protocols through on-chain smart contracts, which combine on-chain execution with off-chain legal enforcement, all powered by Story. The Agent TCP/IP protocol lays the foundation for future agents to realize their role as independent economies. Agents can improve themselves with authorized training data and registered IP, and then monetize outputs. As more and more agents join the network, the value and capabilities of the entire ecosystem will increase exponentially. Each new agent brings unique capabilities and combines with the advantages of existing agents to produce new solutions and services. For example, some specialized agents can co-produce movies, where the producer agent hires screenwriter agents and video generation agents and distributes revenues according to their on-chain protocols.
3.3 IP Tokens
Story's native token - IP, coordinates all value flows and runs through the entire peer-to-peer intellectual property system.
IP acts as the underlying medium of exchange for the network. Whenever intellectual property assets are used, exchanged or generated income, IP achieves efficient processing of transactions and fair distribution of resources through a transparent fee payment mechanism. It not only promotes peer-to-peer direct transactions without intermediary participation, but also serves as a functional tool and a medium of value exchange, helping the growth of the network economy.
In addition, Story adopts a PoS consensus mechanism, and verifiers need to stake IP to ensure network security. Verifiers are responsible for processing transactions and maintaining the integrity of the blockchain, and receive IP-denominated rewards based on their performance. This provides a strong incentive for validators to operate in an honest and efficient manner as they are closely related to the success of the network, thus strengthening IP’s position as the foundation of Story security.
As a unified utility token, IP assumes the dual function of maintaining network security and ecosystem functions, closely combining network operations with the broader intellectual property market. As Story's gas, staked and utility tokens, IP plays a key role in incentivizing all participants in the Story ecosystem and promoting the maintenance and development of point-to-point intellectual property systems.
In the wider ecosystem, IP aims to play a more critical role in protecting IP assets, acting as a currency for intellectual property revenue streams, and even providing a native medium of exchange for AI agents that settle their IP on Story. The PoC protocol and other dedicated protocols deployed on the IP core all rely on IP as the basis for operation. IP promotes all value transfers within the IP core, including royalty allocations, licensing fees and usage-based compensation. This integration means that IP functions beyond basic cybersecurity – it is the cornerstone of protecting and verifying all intellectual property assets registered on Story. More importantly, the Agent TCP/IP protocol utilizes IP to provide a strong security layer, ensuring communication between agents, and at the same time provides a native mechanism for efficient value exchange between agents. This dual function ensures that AI agents can conduct economic transactions and communications automatically without trust.
IP is a unified utility token for cybersecurity and ecosystem functions, combining network operations with a wider intellectual property market. As Story's gas, staking and utility tokens, IP plays a vital role in incentivizing all participants in the Story ecosystem and maintaining and expanding peer-to-peer intellectual property systems.
in conclusion
We have launched a point-to-point intellectual property system that breaks the dependence on centralized institutions. The Story blockchain provides a dedicated network that can create both a common repository of intellectual property assets and a programmable market for IP asset exchange. Story's multi-core architecture provides the necessary scalability and professional support to cope with the ever-evolving application integration and artificial intelligence scenarios. A full-network intellectual property map embedded in the Story blockchain accurately depicts the complex relationship between various intellectual property assets and provides a sound record of economic commitments. With the accelerated development of artificial intelligence, the scale and liquidity of intellectual property rights are also expanding, and the network built by Story will become the pillar of the new intelligent economy. As digital gold, Bitcoin acts as the value carrier of all commodity assets, and Story provides a store of value for all knowledge assets in the form of programmable intellectual property rights.
Acknowledgements
The Story Foundation thanks a16z crypto, especially Eddy Lazzarin and Scott Kominers for their fundamental support in the early stages of the Story network and PoC protocol design. In addition, the author would like to thank Jason Yanowitz, Chainyoda and Scott Kominers for their feedback during the drafting of this white paper.
Appendix A - PoC Protocol
The Proof of Creativity protocol introduces an open programmable IP protocol that elevates intellectual property (IP) into an important part of the blockchain ecosystem. At the heart of this protocol are IP assets and their associated IP accounts, a smart contract account that serves as the core identity of each intellectual property.
This account-centric design makes the storage and management of IP data more convenient, and the interaction and operation with these data is achieved through modular functions. These modules extend the capabilities of the protocol, enabling creators and users to easily manage and authorize their IP in a decentralized and programmable environment.
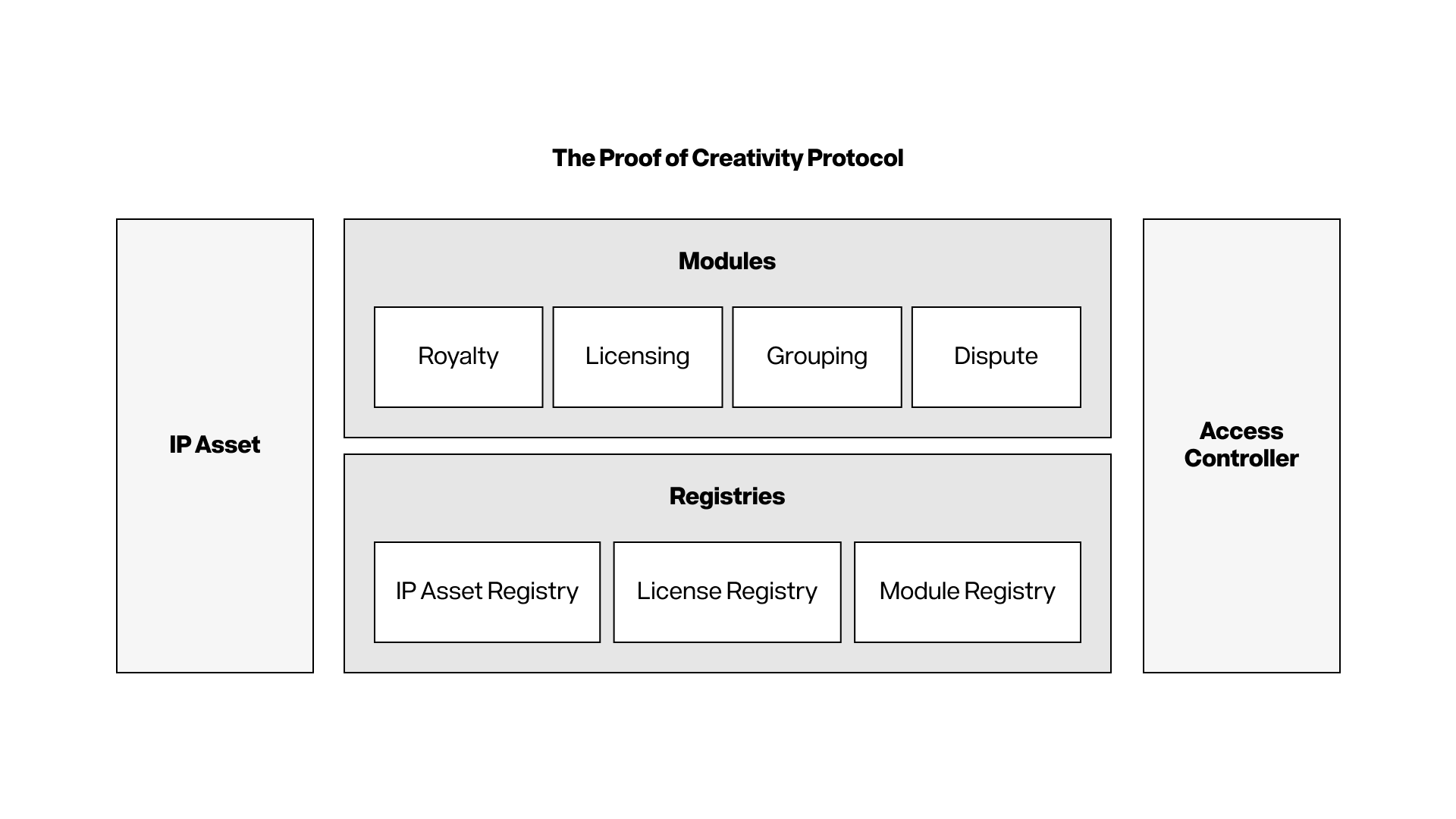
To achieve this goal, the protocol consists of two parts: data structure and module. The data structure is equivalent to the "noun" in the protocol, which stores metadata related to IP, namely "IP Lego". The module is a "verb" that provides multiple functions for IP assets registered in the protocol.
Data structure (noun)
IP assets are the underlying “IP Lego” in the PoC protocol. Each IP asset represents an IP on a chain and its associated IP account, which is based on a modified version of ERC-6551 (token-bound account). IP assets convert a new or existing NFT into an IP entity with multiple functions and interactivity, representing tokenized intellectual property.
An IP account is a programmable account mapped to a tokenized IP. It has modified ERC-6551 and has the common "execute()" function, allowing any module in the protocol to be called by compiling byte data, which provides the possibility for future module expansion.
Module (verb)
Modules (i.e., verbs) are customized smart contracts used to define and extend the functionality of IP assets in the PoC protocol.
Authorization module
The authorization module is a core part of the agreement, enabling IP holders (as authorized parties) to create and manage authorization agreements using license tokens and their related terms. The license terms are derived from preset authorization templates. For derivative works, the licensing terms of the parent IP will also be taken into account during the licensing process. The end result is to mint a license token.
The PoC protocol introduces Programmable IP License (PIL) as an off-the-shelf licensing template, aiming to provide IP holders with a common and easy-to-adoption licensing framework, simplify the licensing process, and establish a standardized legal framework.
Programmable IP License (PIL)
License templates are a legal framework ("programmable") compiled in smart contracts that define various licensing terms of IP. The terms and conditions may include commercialization, transferability, or royalty percentage.
Programmable IP License (PIL) was developed by the Story team ([14]), and is the first instance of this license template. Although the issuance of IP Agreement (IPA) terms and license tokens occur on the chain, these contents are enforced under the off-chain legal framework. This legal contract enables to integrate tokenized IP assets into the traditional legal system and provides creators with clear guidance on how they can remix, monetize, and create derivative works.
Royalties module
The royalty module is used to manage the income distribution between child IP assets and their parent IP assets. It allows the IP holder (as authorized) to define the proportion of revenue the child IP pays to the parent IP. Similarly, as a child IP holder of the authorized party, the proportion of revenue paid by the derivative IP to its child IP can be specified.
After the income is paid to IP assets, it will be deposited into the IP royalty vault. Each IP asset has an independent royalty vault, and the royalty token holder has the right to withdraw funds from the vault in proportion.
The royalty module supports a variety of customizable royalty payment structures. By default, each parent IP asset can set a minimum royalty ratio. This ratio determines the revenue share that derivative IPs at all levels in the derivative chain need to be allocated to the parent IP according to the license agreement.
Dispute module
The dispute module provides users with a framework for resolving disputes. Its arbitration system consists of two main components:
-
Arbitration Policy: Arbitration Policy defines the rules, processes and responsible entities for resolving disputes.
-
Arbitration Penalty: The consequences required for the arbitration Penalty to determine the IP assets “labeled” as part of the dispute.
