Not 360 but Bitcoin who protect the deepseek

Reprinted from jinse
02/02/2025·2MIs DeepSeek good? When Deepseek recovered from the DDOS attack of the entire network, we found Bitcoin in the Deepseek interface request after returning the soul .
And listen to me slowly.
1. Deepseek card burst
Deepseek is encountered in the largest DDOS attack.
According to rumors, the peak of the attack exceeded 3.2Tbps, which is equivalent to tens of millions of devices per second at the same time "knocking" at the same time, resulting in its newly released R1 model service for nearly 1 day.
DeepSeek came over. Whose credit?

Some people say that it is the older generation of Internet companies 360 security brain, Huawei Yun's Taishan prevention and control, Alibaba Cloud computing power scheduling algorithm, Haikang Public surveillance algorithm, Netease game thunder fire game server cluster, urgent communication pool, rookie network logistics dispatch Algorithms, Red Guest Alliances and other combination of multi -level and multi -dimensional traffic cleaning to protect the descendants of Deepseek.
Please, I hope you don't believe it. In addition to Zhou Hongyi's tirelessly touched the porcelain Deepseek, I think other large manufacturers are aggressive.
Behind this "digital riots" is actually the epitome of the network security offensive and defensive war -the attacker controls the "Zombie Legion" to launch a tide -like request, and the defense needs to find the way to break the situation in the game of computing power and wisdom.
It's really difficult.
But it is interesting that DeepSeek's breaking key is not in Shuangwen, but in Bitcoin.
Second, iron syndrome like mountains
At first, I was just curious. After the recovery, Deepseek started to turn around for a long time, and the computer's fan began to start at full speed. From the perspective, this is much like the bitcoin mining we know.
It wasn't until I opened the F12 and saw DeepSeek's request existing Create_Pow_Challenge that I realized that the original Deepseek was using Bitcoin POW mechanism to fight DDOS attacks.
Is it true? Let me ask the classmates of DeepSeek
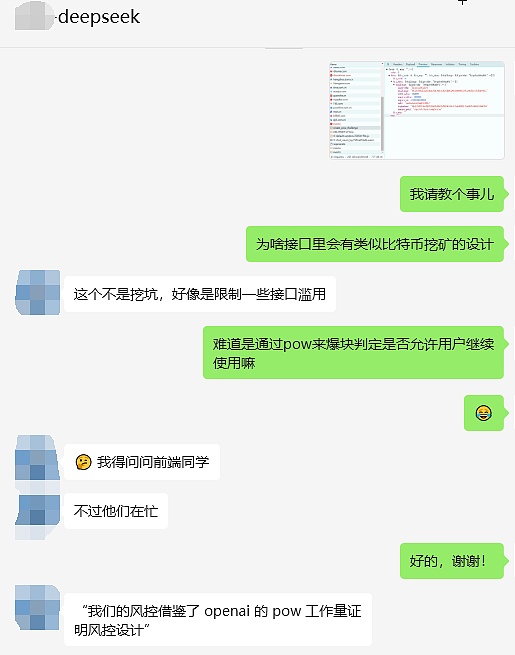
It is true , not only uses it, but also is also used.
So why is Bitcoin?
3. Enlightenment of Bitcoin
The essence of DDOS attack is to submerge the target system through massive invalidation, until the target system is overwhelmed and refuses to serve.
Traditional defense methods such as traffic cleaning and IP ban can alleviate the symptoms, but it is difficult to cure the root cause -low attack cost and high defense cost, just like "fighting flood with fire hydrants".
The new strategy of DeepSeek borrowed from Bitcoin's workload certificate (POW) mechanism. To put it simply, if users want to call AI services, they need to complete a calculation question (similar to Bitcoin mining) before the successful problem -solving can get the "pass". This design allows each request to pay the cost of real computing power. If an attacker wants to launch a large -scale attack, the cost will increase the index level.
What is the logic behind this?
Bitcoin ensures network security through POW: Miners consume computing power in exchange for accounting. If an attacker wants to tampering with data on the chain, it is necessary to control the computing power of more than 51%of the entire network, and the cost far exceeds the income. DeepSeek migrates this logic to the field of risk control -if an attacker wants to forge massive requests, it needs to pay the equivalent computing power price as the real user, and this will have no economy for attackers.
This is too great.
Fourth, the other side of the coin
DeepSeek's attempt revealed a trend: the underlying philosophy of the blockchain is reshaping network security. POW's "economic game" thinking provides a new paradigm for confrontation of distributed attacks -no longer relying on technical suppression, but to make attackers "actively abandon" through mechanism design.
Just as Bitcoin uses decentralization to confront financial monopolies, DeepSeek competes against the torrent of traffic with computing power. This may be the charm of technology: seemingly irrelevant areas often hidden the key to solving problems.
In the end, the essence of security is not to build a wall, but to make the damage cost higher than the income. The "cross -border cooperation" of DeepSeek and Bitcoin may be the best annotation of this logic.
May you have both Deepseek and Bitcoin.


 panewslab
panewslab