Web3 security introduction to avoid pits: How to ensure the safety of the clipboard?

Reprinted from panewslab
04/18/2025·10DAuthor: Liz & Reborn
Editor: Sherry
background
In the previous issue of Web3 security introduction to avoid pits, we analyzed the Pixiu disk scam, and this issue we will focus on clipboard security.
Among many crypto asset theft incidents, the most confusing thing about victims is often: "I have not transmitted a private key online at all, so why are I stolen?" In fact, the leakage of private key/mnemonic words does not necessarily upload through the cloud or the Internet, it may also happen in your seemingly "local, secure" operations. For example, have you ever filled in the private key/mnemonic word by copying and pasting? Have you ever saved it in a memo or screenshot? These common operations are also breakthroughs that hackers are targeting.
This issue will focus on clipboard security, taking you through its principles, attack methods, and the prevention suggestions we have summarized in practice, helping users build a more stable sense of asset protection.

Why are there risks in clipboards
The clipboard is a temporary storage space provided by the operating system for local applications to share. It is mainly used to store temporary data (such as text, pictures, file paths, etc.) so that content can be easily copied and pasted between different applications. For example, when you copy a wallet address, the operating system stores the address in the clipboard until it is overwritten or emptied by new content.
- Plaintext Storage: Most operating systems (such as Windows, macOS, and Linux) do not encrypt clipboard data by default, but store it in memory in plaintext.
- System API provides access: Most operating systems provide clipboard-related APIs that allow applications to access the clipboard. This means that if an application (such as text editors, browser extensions, input methods, screenshot tools, and even malware) has corresponding permissions, it can silently read or even tamper with data in the background.
Moreover, since the content of the clipboard is not automatically cleared by default, it may remain accessible for a longer period of time. If the user copied sensitive information but did not overwrite or clear it in time, malware or third-party applications have the opportunity to read the content.
Some clipboard malware is specifically used to tamper with addresses. The 2024 fraud report on transnational organized crime in Southeast Asia released by the United Nations Office on Drugs and Crime mentioned that one of the commonly used malware in Southeast Asian criminal groups is the cutter. This software monitors the clipboard of the infected system, waiting for an opportunity to replace the address in the cryptocurrency transaction, and once the victim makes an unintentional transaction, it transfers the funds to the attacker's address. Since encrypted wallet addresses are usually very large, users will not notice changes in the collection address.
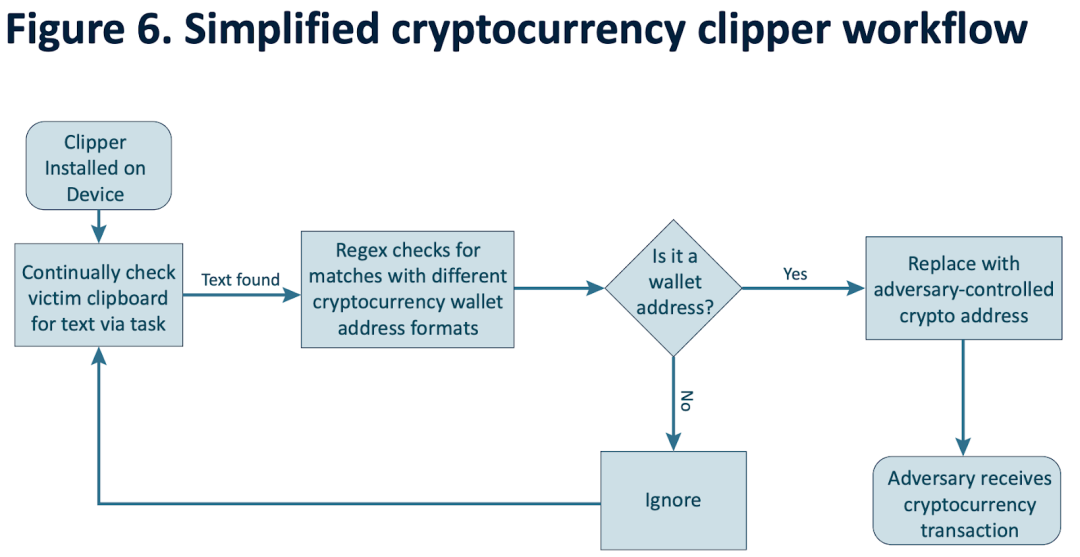
(https://www.unodc.org/roseap/uploads/documents/Publications/2024/TOC_Convergence_Report_2024.pdf)
At this point, I believe everyone has realized that the most fundamental way to prevent clipboard attacks is to avoid copying sensitive information and installing professional antivirus software to prevent malware from invading.
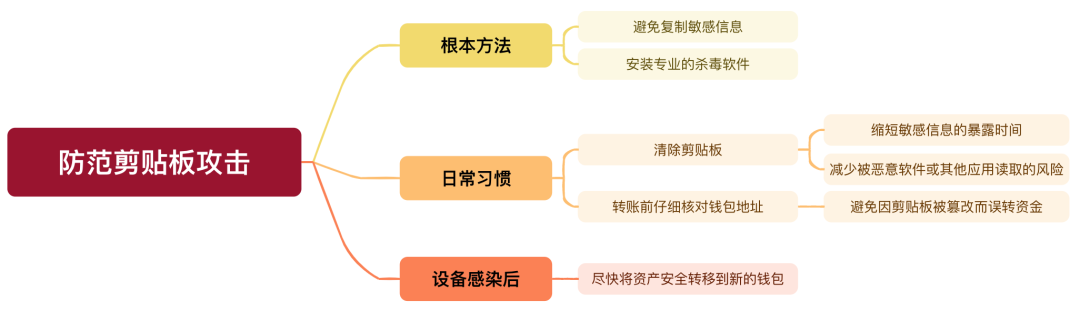
The main function of clearing the clipboard is to shorten the exposure time of sensitive information and reduce the risk of being read by malware or other applications. If you accidentally copy sensitive information, clearing the clipboard in time can reduce the possibility of leakage. An easy way is to copy a large piece of irrelevant content immediately and "flush out" the sensitive information copied previously, which can reduce the probability of being read to a certain extent.
But if your device is already infected with malware that can steal or tamper with clipboard content, manually clearing the clipboard is limited. Because these malicious programs can monitor and read data in real time, manual clearance is difficult to catch up with their operations. Therefore, it is best to avoid copying sensitive information from the source and ensure the device is safe. If you suspect that the device has been infected, it is recommended to transfer the assets safely to a new wallet as soon as possible to prevent further losses.
In addition to clipboards, sensitive information may also be leaked through the following methods, and users need to pay more attention to:
- Album, cloud storage, input method: Avoid private keys/mnemonic words touching the Internet, including but not limited to albums, clouds, WeChat collections, mobile phone memos, etc., and avoid entering sensitive information in the input method. It is recommended to use the system's own input method and turn off the "cloud synchronization" function of the input method, and try not to fill in the private keys/mnemonic words by copying and pasting.
- Malware risk: Use antivirus software to scan the system regularly to detect potential malware.
- Browser extension permissions issue: Disable unnecessary browser extensions. If you are worried about the permission risks of a certain extension, you can not use it after installing the extension. Look at the extension ID, search for the local path of the computer, find the manifest.json file in the extension root directory, and send the file content to the AI for permission risk interpretation. If you have isolation thinking, you can consider enabling Chrome Profile for strange extensions separately, at least evil is controllable.
- Transfer address tampering risk: When performing cryptocurrency transfer and other operations, be sure to carefully check the wallet address to avoid mistransferring funds due to clipboard tampering.
Clipboard cleaning tutorial
Here are some simpler ways to clear the clipboard for macOS, iOS, Android, and Windows. You can practice it:
macOS only saves the current clipboard content, does not record history, copying an irrelevant piece of content can overwrite sensitive history. iOS also only saves the current clipboard content. In addition to copying an irrelevant piece of content, users can also create shortcuts to add the clipboard clearing command to the home screen, which makes it more convenient to clear.
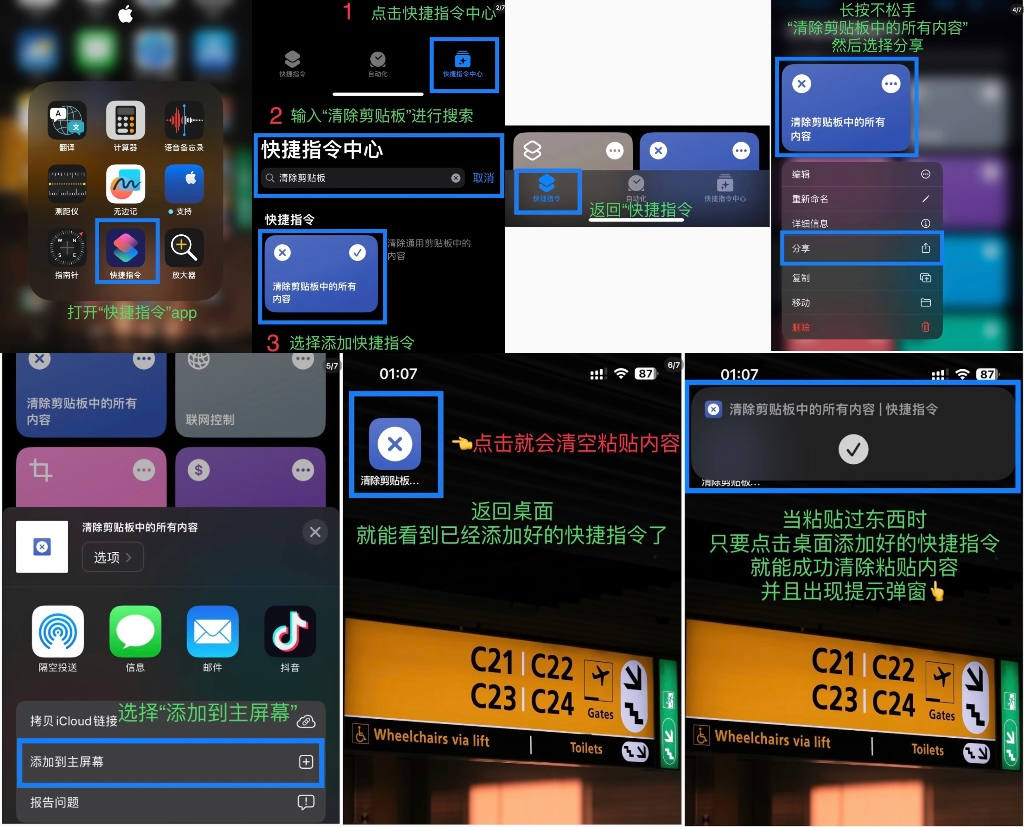
(https://x.com/0xBeyondLee/status/1855630836118467028)
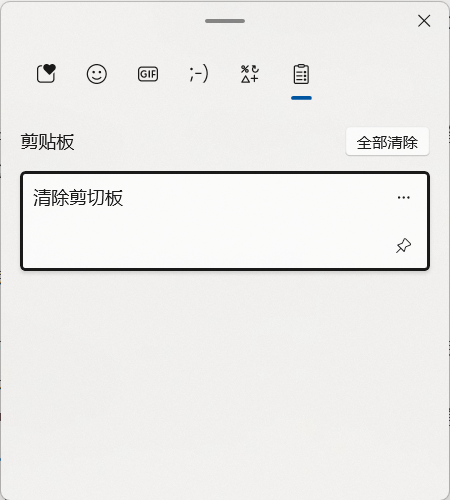
Windows 7 and earlier versions only save the current clipboard content without history. You can indirectly clear the original content in the clipboard by copying an unrelated piece of content. Windows 10/11 (If "Clipboard History" is enabled): Press Win + V to view the clipboard history, click the "Clear All" button in the upper right corner to delete all history.
Android's clipboard history usually refers to the clipboard history recorded by the input method. Many Android devices will provide clipboard history functions in the input method, and can enter the clipboard management interface of the input method to manually clear unnecessary records.
In short, if the system itself does not save history, just copy the new content override. If the system has a clipboard history (such as Windows 10/11, some Android devices), then manually clear the history according to the above method.
Summarize
Clipboard is a often overlooked but highly exposed channel. We hope that this issue of the article can help users re-examine the security risks of copying and pasting, and realize that "local operations do not equal absolute security." Safety is not only a technical issue, but also a behavioral habit. Only by staying alert, improving safety awareness in daily operations, and implementing basic protective measures can you truly protect your assets.


 chaincatcher
chaincatcher