Vitalik: How are AI and encryption changing privacy?

Reprinted from chaincatcher
04/15/2025·8DOriginal title: "Why I support privacy"
Author: Vitalik Buterin, founder of Ethereum
Translated by: Baishui, Golden Finance
Special thanks to Balvi volunteers Paul Dylan-Ennis, pcaversaccio, vectorized, Bruce Xu and Luozhu Zhang for their discussion and feedback.
Recently, I have been increasingly concerned about improving the privacy of the Ethereum ecosystem. Privacy is an important guarantee for decentralization: whoever has the power to grasp the information, so we need to avoid centralized control of information. In the real world, people's concerns about centralized technology infrastructure are sometimes worried that operators will accidentally change rules or remove user platforms, but it is also common to worry about data collection. While the cryptocurrency space originated from projects like Chaum’s Ecash, which puts the protection of digital financial privacy first, it has recently underestimated privacy, and the reason is ultimately bad: Before the advent of ZK-SNARK technology, we could not provide privacy in a decentralized way, so we downplayed the importance of privacy and focused on other assurances we could provide at the time.
However, privacy is now impossible to ignore. Artificial intelligence is greatly improving the ability to collect and analyze centralized data, and also greatly expanding the scope of data we voluntarily share. In the future, new technologies such as brain-computer interfaces will bring more challenges: we may really talk about artificial intelligence understanding our ideas. At the same time, we have more powerful tools to protect privacy than 1990s crypto-punk could imagine, especially in the digital realm: efficient zero-knowledge proof (ZK-SNARK) can reveal enough information to prove that we are trustworthy while protecting our identities; full homomorphic encryption (FHE) allows us to calculate data without viewing it; and obfuscation technology may soon provide more functionality.

Privacy does not mean segregating from each other, but unity.
At this point, it is necessary to review this question: Why do we need privacy? Everyone's answer is different. In this post I will give my own answer and divide it into three parts:
- Privacy is freedom: Privacy gives us space to live in a way that meets our needs without always worrying about how our behavior will be viewed in various political and social games.
- Privacy is order: many mechanisms that constitute the basic operation of society rely on privacy to operate normally.
- Privacy is progress: If we can find new ways to share information selectively while protecting it from abuse, we can unleash huge value and accelerate technological and social progress.
Privacy is freedom
As early as the early 21st century, views similar to those summarized in David Bryn's 1998 book Transparent Society were prevalent: technology will make information around the world more transparent, and although this will bring some disadvantages and requires constant adjustment and adaptation, it is a very good thing in general, and we can make it more fair by ensuring that the people can monitor (or rather, monitor) governments. In 1999, Sun Microsystems CEO Scott McNeley made a famous remark: "Privacy is dead, accept it!" This mentality was very common in Facebook's early conception and development, when Facebook banned the use of pseudonym identities. I personally remember that at an event at Huawei in Shenzhen in 2015, a (Western) speaker casually mentioned that "privacy is dead" and personally experienced the end of this mentality.
"Transparent Society" embodies the best and brightest prospects that "privacy has arrived" ideology can provide: it promises a better, just and fairer world, leveraging the power of transparency to hold governments accountable, rather than suppressing individuals and minorities. Yet, in hindsight, even this idea is clearly a product of the times, written at the peak of global cooperation and peace and the "end of history" enthusiasm, and it relies on a series of overly optimistic assumptions about human nature. Mainly manifested in:
- The top levels of global politics will often be kind and sensible, making vertical privacy (i.e., not revealing information to powerful people and institutions) increasingly unnecessary. Abuse of power is often confined to specific areas, so the best way to combat these abuses is to expose them to the sun.
- Culture will continue to improve until horizontal privacy (i.e., not revealing information to other members of the public) becomes no longer necessary. Nerds, homosexuals, and eventually everyone else can stop hiding in the cabinet, because society will no longer be harsh and judge people’s unique traits, but will become more open and inclusive.
Nowadays, no major country can generally agree that the first assumption is correct, while many major countries generally believe that it is wrong. In the second aspect, cultural inclusion is also rapidly regressing – just searching for phrases like “bullying is a good thing” on Twitter is evidence, although it is easy to find more similar evidence.
I personally unfortunately encounter the disadvantages of a "transparent society" often because every move I do outside may unexpectedly become a public report in the media:

The worst part is that someone took a one-minute video while I was using my laptop in Chiang Mai and posted it on Xiaohongshu, which immediately received thousands of likes and retweets. Of course, my own situation is far from the norm of humanity—but privacy has always been like this: people with relatively normal living conditions do not need privacy, while people with deviant life conditions need privacy more, no matter what the deviates from the direction. Once you add up all the important directions, there are quite a few people who really need privacy – you never know when you will be one of them. This is also an important reason why privacy is often underestimated: it is not only about your situation and information today, but also about unknowns on what will happen to that information in the future (and how it affects you).
Today, even among AI advocates, the privacy of enterprise pricing mechanisms is a niche issue, but with the rise of AI-based analytical tools, it could become an increasingly serious problem: the more companies know you, the more likely they will be to offer you personalized prices, maximizing the profits they squeeze out from you multiplied by your chances of paying.
I can express my general argument about privacy, freedom, in one sentence, as follows:
Privacy gives you the freedom to live in a way that best suits your personal goals and needs without constantly balancing every action between "private games" (your own needs) and "public games" (various others, through various mechanisms including social media cascades, business incentives, politics, institutions, etc., will see and respond to your behavior).
Without privacy, everything becomes an ongoing struggle, with the focus of the debate being “what others (and robots) will see what I do” – whether it’s powerful people, companies, or peers, now or in the future. With privacy, we can keep our balance. Today, this balance is rapidly eroding, especially in the physical realm. The default path of modern tech capitalism, the desire to find a business model that can obtain value from users without explicit payment, is further eroding this balance (even penetrates into highly sensitive areas, such as eventually penetrating into our own thoughts). So we need to offset this impact and support privacy more clearly, especially in the areas where we can do it most: the digital world.
But why not allow the government to have backdoors?
There is a common response to the above reasoning: the privacy drawbacks I describe are largely due to the over-understanding of our private lives, and even if it involves abuse of power, it is also due to the over-understanding of businesses, bosses and politicians. But we won't let the public, businesses, bosses and politicians have all this data. Instead, we will have a small group of trained, heavily scrutinized law enforcement professionals view eavesdropping data from street surveillance cameras as well as internet cables and chat applications, and perform strict accountability procedures so that others won’t find out.
This is a silent but widely held position, so it is crucial to address this issue clearly. Even if implemented with high quality standards out of good intentions, such strategies have inherent instability for the following reasons:
- In fact, not only the government, but also various corporate entities are facing the risk of data breaches, and the quality is uneven. In traditional financial systems, KYC and payment information are in the hands of payment processors, banks and various other intermediaries. The email provider will view a massive amount of various data. Telecom companies know your location and resell them illegally regularly. Overall, it is possible that all of these entities are strictly regulated enough to ensure that they truly value user data, which is a huge effort for both monitors and those under monitoring, which may be out of place with maintaining competitive free markets.
- Individuals with access always feel misused data (including sales to third parties). In 2019, several Twitter employees were charged with selling personal information from dissidents to Saudi Arabia and were subsequently convicted.
- Data may be hacked at any time. In 2024, data that US telecom companies must collect according to law was hacked, allegedly caused by hackers from the Chinese government. In 2025, a large amount of sensitive personal data held by the Ukrainian government was hacked by Russian hackers. On the other hand, China's highly sensitive government and enterprise databases have also been hacked, including the US government.
- The regime may change. A government that is trustworthy today may no longer be trustworthy tomorrow. Those in power today may be persecuted tomorrow. A police agency, which still maintains impeccable standards of respect and etiquette today, may become a cruel act of gloating in ten years.
From an individual perspective, if their data is stolen, they cannot predict whether and how it will be abused in the future. By far the safest way to handle large-scale data is to collect as little data as possible from the start. Data should be held to the maximum extent by the user and encryption is used to summarize useful statistics without compromising personal privacy.
Some people believe that the government should have the right to obtain any information with a search warrant because things have always worked like this, and this statement ignores a key point: historically, the amount of information obtained by search warrants is much lower than today, or even less than what can be obtained if the strictest Internet privacy protection measures are generally adopted. In the 19th century, on average, each person had only one voice conversation and was never recorded by anyone. Therefore, the moral panic caused by "information privacy" is completely inconsistent with historical laws: ordinary dialogue, even financial transactions, and completely and unconditionally maintaining privacy is the historical norm for thousands of years.

A normal conversation in 1950. No one has recorded, monitored, “legitimately intercepted,” conducted AI analysis, or otherwise viewed the conversation at any time, except those involved in the conversation.
Another important reason to minimize centralized data collection is that a large part of global communications and economic interactions are inherently international. If everyone is in the same country, then to say the least, the "government" should have access to the data in their interactions. But what if people are in different countries? Of course, in principle you could try to come up with a "Galaxy Brain" scheme that maps everyone's data to a legal access entity responsible for them - even so, you have to deal with a large amount of edge cases involving multiple people's data. But even if you can do it, this is not the realistic default result. The reality of government backdoors is that the data is concentrated in a few central jurisdictions that have everyone’s data because they control the application—essentially global technological hegemony. Strong privacy is by far the most stable alternative.
Privacy is order
For more than a century, it has been recognized that the key technical element in which democratic institutions work effectively is secret voting: no one knows who votes you vote, and even if you really want to prove it, you can't prove to anyone who votes you voted. If secret voting is not the default setting, voters are subject to various side incentives that affect their voting methods: bribery, retroactive reward commitments, social pressure, threats, and more.
It can be seen from a simple mathematical argument that this kind of side incentive will completely undermine democracy: in an election with N people, your probability of affecting the outcome is only about 1/N, so any consideration about which candidate is better and which candidate is worse will be divided by N. Meanwhile, "side games" (e.g., voter bribery, coercion, social pressure) will directly affect you based on how you vote (rather than based on the overall voting results), so they will not be divided by N. Therefore, unless the accompanying game is strictly controlled, they will by default overwhelm the entire game, drowning out any considerations about which candidate's policy is actually better.
This applies not only to democracy on a national scale. In theory, it applies to almost all corporate or government agency issues:
- Judges decide how to decide a case
- Government officials decide which company to sign a contract or grant
- Immigration officials decide to issue or reject visa
- Social media company employees decide how to implement content review policies
- Company employees participate in business decisions (e.g., which supplier to purchase from)
The fundamental problem in all cases is the same: if the agent acts honestly, they can only bring a small part of the benefit from their actions to the entity they represent; and if they follow some incentives of the accompanying game, they can gain the full benefit. So even today, we still need a lot of moral goodwill to ensure that all our institutions are not completely swallowed up by a chaotic vortex of a back-to-back game. If privacy is further weakened, these collateral games will become stronger and the moral goodwill required to maintain the normal functioning of society may become unrealistic.
Can the social system be redesigned to avoid this problem? Unfortunately, game theory almost explicitly states that this is impossible (with one exception: total dictatorship). In a game theory version focusing on individual choices—that is, the possibility that each participant makes decisions independently and does not allow multiple subject groups to work together for the common good—mechanical designers have great freedom to "design" the game to achieve various specific results. In fact, there is mathematical proof that any game must have at least one stable Nash equilibrium, so analyzing such games becomes easy to deal with. But in the game theory version that allows the possibility of alliance cooperation (i.e. "collusion"), that is, cooperative game theory, we can prove that there are a large number of games without any stable results (called "core"). In such a game, no matter what the current situation is, there are always some alliances that can make a profit from it.

If we take mathematics seriously, we will conclude that the only way to establish a stable social structure is to put some restrictions on the amount of coordination that may occur among participants—which means a high degree of privacy (including deniality). If you don't take mathematics itself seriously, then looking at the real world, or at least thinking about what some of the above-mentioned agency situations will turn out to be if taken over by the edge game is enough to draw the same conclusion.
Note that this leads to another argument about why government backdoors are at risk. If everyone has unlimited abilities to coordinate with others in everything, the result is chaos. But if only a few people can do this because they have the privilege of accessing information, then the result is that they dominate. One party has a backdoor to get another party’s communications, which easily means the end of the feasibility of a multi-party system.
Another important example of a social order that can only function by restricting co-conspiracy is intellectual and cultural activities. Participation in knowledge and cultural activities is essentially a public welfare activity driven by intrinsic motivation: it is difficult to find external incentives designed to make positive contributions to society, precisely because knowledge and cultural activities are, to some extent, an activity that determines which behaviors in society are positive behaviors. We can develop some approximate business and social incentives to guide the right direction, but they also require strong complements of intrinsic motivation. But this also means that such activities are very susceptible to external motivation imbalances, especially marginal games such as social pressure and coercion. To limit the impact of external motivations of such imbalances, privacy is once again necessary.
Privacy is progress
Imagine a world where public and symmetric key encryption is completely non-existent. In this world, sending messages safely at a distance can become more difficult in nature—not impossible, but very difficult. This will lead to a significant reduction in international cooperation, and as a result, more cooperation will still be carried out through face-to-face offline channels. This will make the world poorer and more inequality.
I think that this is the situation we are in today relative to the hypothetical future world, when stronger forms of cryptography will be widely used – especially programmable cryptography, supplemented by stronger full-stack security and formal verification, thus providing us with strong assurance that these cryptography are used correctly.

Egyptian God Protocol: Three powerful and highly versatile structures that allow us to calculate data while keeping it completely private.
Healthcare is a great example. If you talk to people who have worked in the last decade in longevity, fighting the pandemic or other health fields, they will unanimously tell you that future treatment and prevention will be personalized, and effective responses are highly dependent on high-quality data, including personal and environmental data. To effectively protect people from airborne diseases, it is necessary to understand which areas have higher and lower air quality and where pathogens appear at specific times. The most advanced longevity clinics provide customized advice and treatment options based on data about your body, dietary preferences and lifestyle.
However, all of this poses a huge privacy risk at the same time. I personally know about an incident where a company equipped an air monitor for an employee who "calls home" and collected enough data to determine when the employee had sex. For similar reasons, I expect many of the most valuable data will not be collected by default precisely because people are afraid of privacy risks. Even if the data is indeed collected, it is almost always not widely shared or made available to researchers—partially for commercial reasons, but equally common is for privacy concerns.
The same pattern has also happened again in other fields. The documents we write, the messages sent on various applications, and the various behaviors on social media all contain a lot of information about ourselves that can be used to more effectively predict and provide what we need in our daily lives. In addition, there is a lot of information about how we interact with the physical environment that is not related to healthcare. Today, we lack the tools to effectively utilize this information without creating a dystopian privacy nightmare. But in the future, we may have these tools.
The best way to solve these challenges is to use strong encryption technology, which allows us to gain the benefits of sharing data without negative impact. In the age of artificial intelligence, the need to obtain data (including personal data) will only become more important, as being able to train and run "digital twins" locally, enabling them to make decisions on our behalf based on high-fidelity approximations of our preferences, which will bring great value. Ultimately, this will also involve using brain-computer interface (BCI) technology to read high bandwidth inputs from our brains. To avoid leading to a highly centralized global hegemony, we need to find ways to achieve this with respect for privacy. Programmable encryption is the most trusted solution.

My AirValent Air Quality Monitor. Imagine there is a device that collects air quality data, publishes aggregated statistics on an open data map, and rewards you with data—all using programmable encryption to avoid leaking your personal location data and verifying the authenticity of the data.
Privacy can promote progress in social security
Programmable encryption technologies such as zero-knowledge proofs are very powerful because they are like Lego bricks in information flow. They can finely control who can see what information, and more importantly, what information can be viewed. For example, I can prove that I hold a Canadian passport that shows that I am 18 years of age or older without revealing any other personal information.
This makes all kinds of interesting combinations possible. I can give a few examples:
- Zero-knowledge personality proof: Prove that you are unique (through various forms of identity documents: passport, biometrics, identification based on decentralized social graphs) without revealing any other identity information. This can be used for "prove that you are not a bot", various "maximum N value per person" use cases, etc., while fully protecting privacy without exposing rules not being violated.
- Privacy Pools is a financial privacy solution that eliminates bad actors without a backdoor. When spending, users can prove that the source of their tokens is not on the public list of hackers and thefts; only hackers and thieves themselves cannot generate such proofs, so they cannot hide them. Railgun and privacypools.com are currently using this kind of solution.
- Device-side anti-fraud scanning: This does not rely on Zero Knowledge Proof (ZKP), but it feels like it falls into this category. You can use the device's built-in filters (including LLM) to check incoming messages and automatically identify potential false information and scam information. If you do this on the device, the user's privacy is not compromised and can be done in a user-authorized manner, allowing each user to choose which filters to subscribe to.
- Proof of physical sources: Using a combination of blockchain and zero-knowledge proofs, various attributes of items in their manufacturing chains can be tracked. For example, this can price environmental externalities without publicly disclosing the supply chain.

Left picture: Privacy pool diagram. Right: Message Checker application, users can choose to turn on or off multiple filters, from top to bottom: URL check, cryptocurrency address check, and rumor check
Privacy and Artificial Intelligence
Recently, ChatGPT announced that it will begin inputting your past conversations into AI as background information for your future conversations. This trend will inevitably move in this direction: AI is fundamentally useful to look back at your past conversations and gain insights. In the near future, we may see someone developing AI products that invade more in-depth privacy: passively collecting your internet browsing patterns, email and chat history, biometric data, and more.
In theory, your data is private to you. But in practice, this doesn't seem to always be the case:
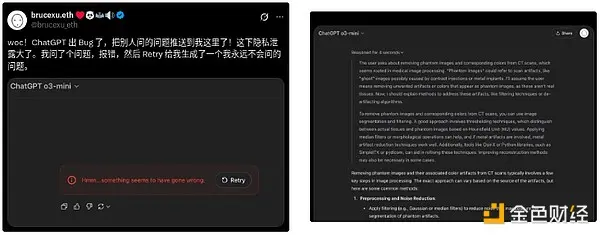
Wow! There is a bug in ChatGPT, which will push the questions asked by others to me! This is a serious privacy leak. I asked a question, then reported an error, and then "try again" generated another question that I would never ask.
It is entirely possible that the privacy protection mechanism works well, and in this case, the AI has hallucinated a question that Bruce never asked and answered. But it is not possible to verify it at present. Similarly, it is impossible to verify whether our conversations are used for training.
All of this is deeply worrying. What is even more disturbing is the explicit monitoring use cases of AI that collect and analyze users’ (physical and digital) data at scale without the user’s consent. Facial recognition technology is already helping authoritarian regimes suppress political dissent on a large scale. And the most worrying thing is the ultimate cutting-edge of AI data collection and analysis: human thinking.
In theory, brain-computer interface technology has amazing power to enhance human potential. Take the story of Noland Arbaugh, the first patient at Neuralink last year:
This experimental device gives Albert, 30, a sense of independence. In the past, someone needed to hold him upright when using a mouth stick. If the mouth stick falls off, someone will need to help him pick it up. And he cannot use it for a long time, otherwise he will develop sores. With the Neuralink device, he has almost complete control of the computer. He can browse the web and play computer games at any time, Neuralink said he has set a record of humans using brain-computer interface (BCI) to control cursors.
These devices are powerful today, enough to help the wounded and sick. In the future, they will be powerful enough to give fully healthy people the opportunity to collaborate with computers and communicate telepathically with each other at an efficiency that we can’t imagine (!!). But truly interpreting brain signals, making this communication possible, requires artificial intelligence.
These trends intertwined, and may naturally spawn a dark future: We will see silicon super agents swallowing and analyzing everyone’s information, including their writing, behaving and thinking. But there is also a brighter future: we can enjoy the benefits of these technologies and protect our privacy.
This can be achieved by combining several techniques:
- Run computations locally as much as possible – many tasks (such as basic image analysis, translation, transcription, basic brain wave analysis of BCI) are simple enough to be done completely in locally run computations. In fact, locally run computing even has advantages in reducing latency and improving verifiability. If something can be done locally, it should be done locally. This includes calculations involving various intermediate steps such as accessing the internet, logging into a social media account.
- Use cryptography to make remote computing completely private—FHE can be used to perform AI calculations remotely without allowing remote servers to view data or results. Historically, FHE is very expensive, but (i) it is rapidly increasing recently, and (ii) LLM is a unique structured form of computation and asymptotically almost all are linear operations, making it ideal for ultra-efficient FHE implementations. Computation involving multiple private data can be done through multiple calculations; common two-party situations can be handled extremely efficiently through technologies such as obfuscated circuits.
- Using hardware verification will guarantee extension to the physical world—we can insist that the hardware that can read our minds, whether from inside or outside the skull, must be open and verifiable, and use techniques like IRIS to verify it. We can do this in other areas, for example: We can install security cameras, which proves that video streams are saved and forwarded only when a local LLM marks it as a physical violence or medical emergency, and deleted in all other cases, and use IRIS for community-driven random checks to verify that the camera is implemented correctly.
Unfinished future
In 2008, liberal philosopher David Friedman wrote a book called "The Imperfect Future." In the book, he outlines the changes that new technologies may bring to society, but not all changes are beneficial to him (or to us). In one of the sections, he describes a potential future: There will be a complex interaction between privacy and surveillance, and the growth of digital privacy will offset the growth of real-world surveillance:
If a video mosquito is lying on the wall watching me typing, then it makes no sense to force encryption of my email. So in a transparent society, strong privacy protection requires some way to protect the interface between my real space body and cyberspace…a low-tech solution is to type under the hood. A high-tech solution is to establish some kind of connection between the mind and the machine, which is not through the fingers—or any channel visible to the outside observer.
The conflict between real-life spatial transparency and cyberspace privacy is also reflected in another direction… My handheld encrypts my information with your public key and transmits it to your handheld, which decrypts the information and displays it through your VR glasses. To make sure nothing reads the glasses from your shoulders, instead of showing the image through the screen, goggles write it to your retina with a mini laser. If you are lucky, your eyeball is still private space inside.
We may end up living in a world where physical activities are completely open and information transactions are completely private. It has some attractive features. Ordinary citizens can still use their strong privacy advantages to find killers, but the cost of hiring a killer may exceed their ability to bear, because in a world that is transparent enough, all murders will be solved. Each killer goes straight to jail after performing a mission.
What about the interaction between these technologies and data processing? On the one hand, modern data processing technology makes transparent society a threat—without data processing technology, it would be useless even if you record everything that happens in the world, because no one can find the six-inch tape he wants in the millions of miles of videotapes produced every day. On the other hand, technologies that support strong privacy offer the possibility of rebuilding privacy, and even in a world with modern data processing technology, there is nothing you can do by protecting your transaction information from being acquired by anyone.
Such a world is perhaps the best of all possible worlds: If everything goes well, we will see a future with little physical violence, but at the same time, our network freedom is maintained and ensures the fundamental functioning of political, civil, cultural and ideological processes in society whose ongoing operation depends on some limitation on the transparency of the full information.
Even if it is not ideal, it is much better than the version that zeroes in physical and digital privacy, ultimately including our own privacy of our own thoughts. By the mid-2050s, we will see some commentary articles that it is certainly unrealistic to expect thinking to be unlawful to be legally intercepted. The response to these commentary articles includes links to a recent incident: a master's degree in law at an artificial intelligence company was exploited, resulting in the leak of private inner monologues of 30 million people in one year on the entire Internet.
Society has always relied on a balance between privacy and transparency. In some cases, I also support privacy restrictions. To give an example that is completely different from what people usually argue in this regard, I support the move to include non-compete clauses in the U.S. government ban contracts, not primarily because they directly affect employees, but because they can force companies to open source implicit domain knowledge. Forced companies to be more open than they want is a limitation on privacy – but I think it is a limitation on net gain. But from a macro perspective, the most pressing risk for technology in the near future is that privacy will approach its all-time lows, and in a very unbalanced way, the most powerful individuals and the most powerful countries will get a lot of data from everyone, and others can hardly see anything. Therefore, supporting everyone’s privacy and making the necessary tools open source, universal, reliable and secure is one of the important challenges of our time.

 panewslab
panewslab